补天: China's digital defense drills
A presentation from 2025 during a 'white hat hacker' conference in China gives an interesting insight into how the government organizes its digital defense.
Last November, a presentation published on the ‘white hat hacker’ forum butian.net, gives an interesting insight into some of China's e-government network architecture and back-end systems. It was part of a presentation held originally during a cyber security conference in the city of Changsha around the same time. The goal of this presentation was to introduce the audience to weaknesses and vulnerabilities of the national e-government system while also providing new ideas how to run better red-team tests to reveal those weaknesses.
Just recently a massive data leak of personal data from a combined set of several government databases holding over 1.2 billion Chinese citizen-data-sets has been revealed. These show that the governments drive to store massive data sets with info on its citizens can be quite perilous if not secured properly.
It gives the impression that the presenter, only introduced there as Rj45mp, has a solid knowledge of the internal organizational and technical components of the administrative networks. He/she was quoting from internal statistics and references diagrams about government cloud infrastructure and technical components that go further than what is usually found in the public domain.
According to his own blog, RJ45mp seems a junior Chinese cyber security professional, living in Shenzhen who is quite active in joining professional red/blue team exercises across the country.
Although it doesn’t hold any smoking-gun-information, it still gives some insights into Chinese red-team tactics. Even if it is only for security auditing. If you are interested in the full set the link to the ‘butian.net’ forum is here.
Starting point
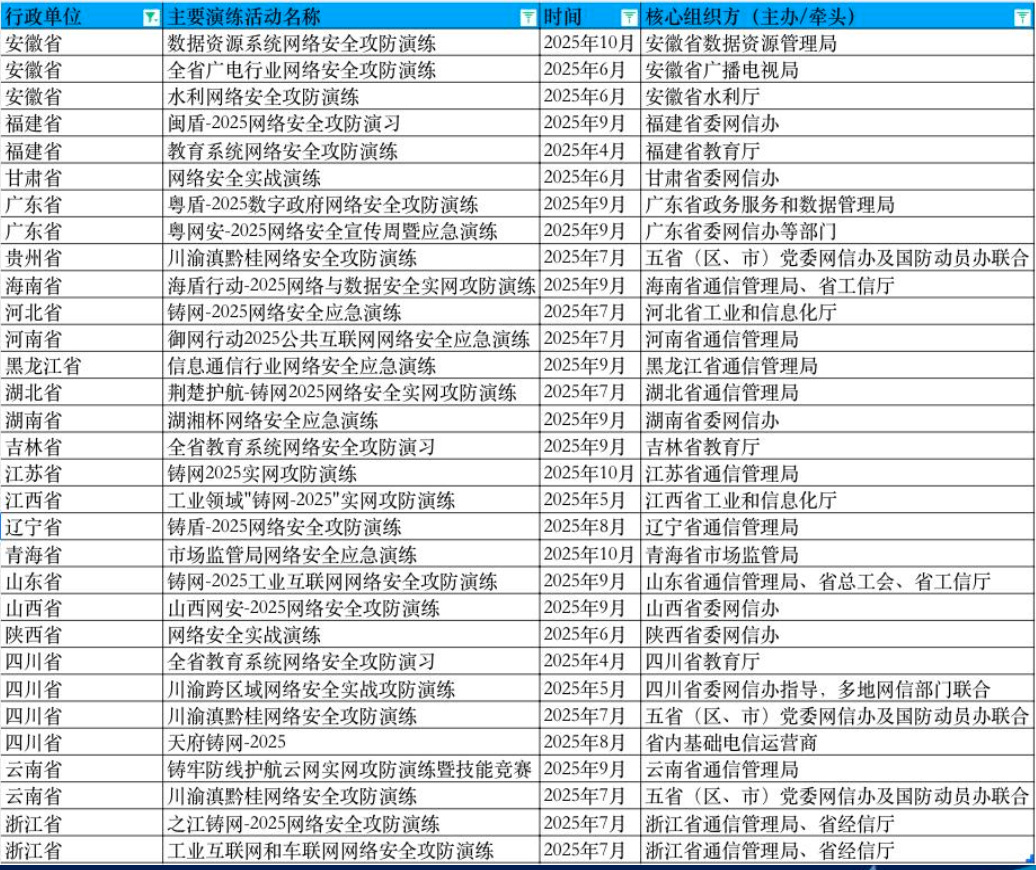
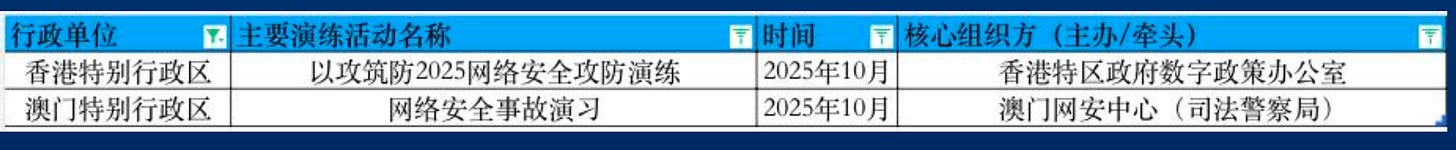
The presentation started off with giving us an overview of the past year on the topic of ‘cyber security drills’ in China. According to the presenter, the government had over 46 of such drills, with a peak in September with 13 drills, including exercises in Hong Kong and Macao.
It also gave the example of three systemic trends, demonstrating the ‘maturity’ of the organizational structure of cyber operations in China, mentioning the three main institutions:
公安系统(执法监督与实战打击:合规审查、拟立案侦查、立案打击 (Public Security System »Law Enforcement Supervision and Practical Crackdown«: Compliance Review, Proposed Case Investigation, Case Filing and Crackdown)
网信办(统筹协调与监督管理:演练“总导演”和“总协调 (Cyberspace Administration of China »Overall Coordination and Supervision«: The Director and Coordinator of the Exercise)
政数局(数字政府时代的新兴主导:演练“靶标提供方”和“核心防守方” (The Bureau of Government Data (an emerging leader in the digital government era): A drill simulating the roles of ‘target provider’ and ‘core defender’.)
Interesting is that we have rarely seen the 政数局 (Bureau of Government Data) before in this context (and as stated above) this seems fairly new.
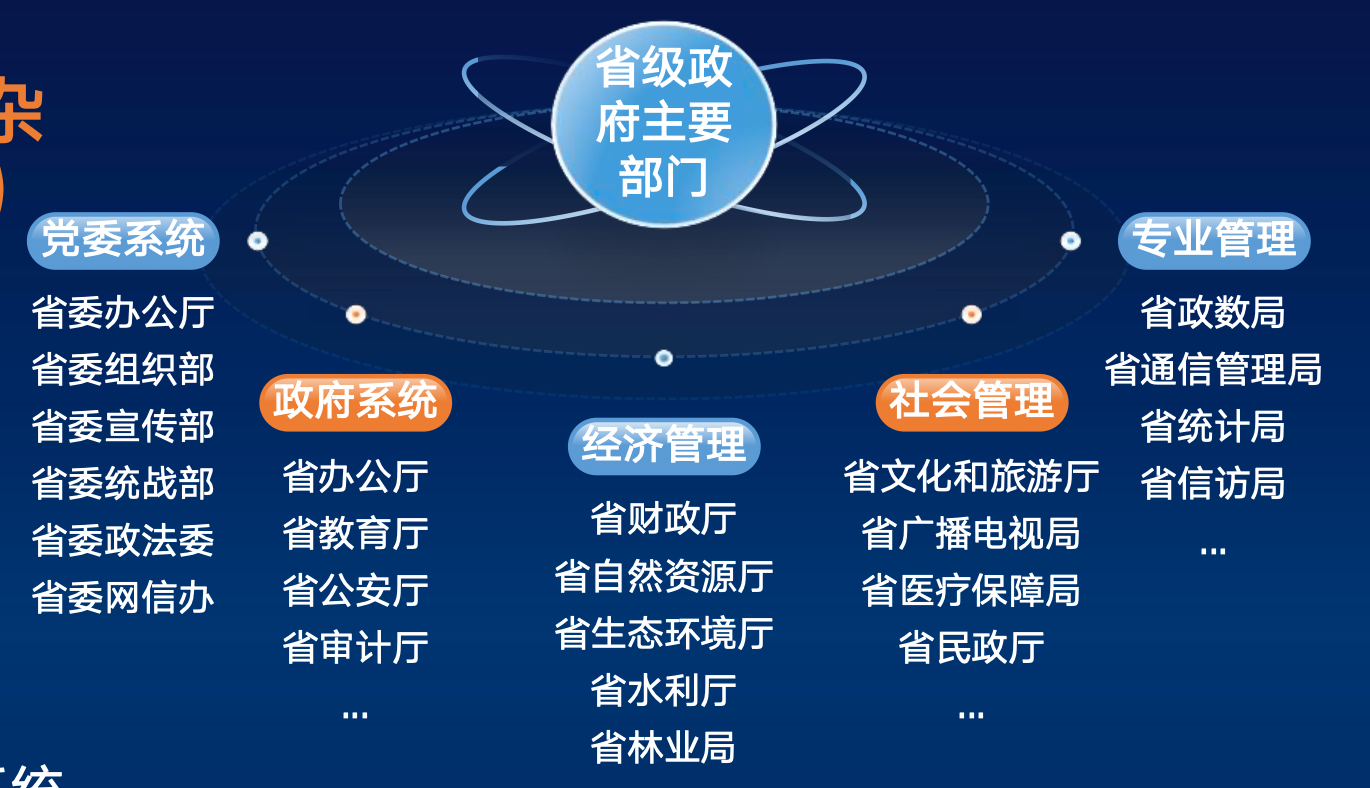
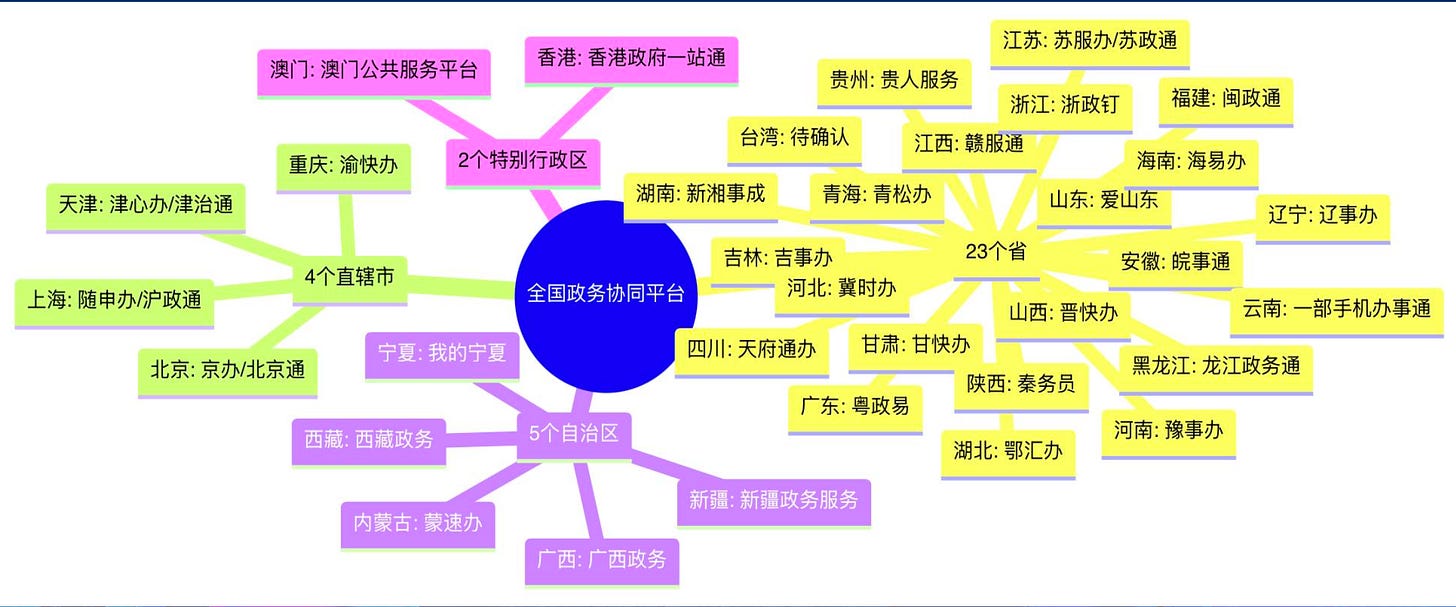
Apparently a lot of work has been going into more heavy integration and collaboration between provincial departments and national departments, standardization of national strategies, workflows and infrastructure. Also, the integration of Hong Kong and Macao into China's national cyber security strategy is often mentioned.
One of the biggest challenges in China's national cyber security landscape was always that there was a lack of coordination, coherence and vastly unbalanced cyber defense capabilities in regional administrations between provinces. This caused a lot of security incidences.
In a country the size of China and a government structure that is at times so ‘decentralized’ and vast, with local power-players fiercely defending their ‘fiefdoms’, making national cyber security capabilities coherent is no small feat. Trying to get rid of this ‘hodgepodge’ is therefore crucial to maintain efficient national cyber security.
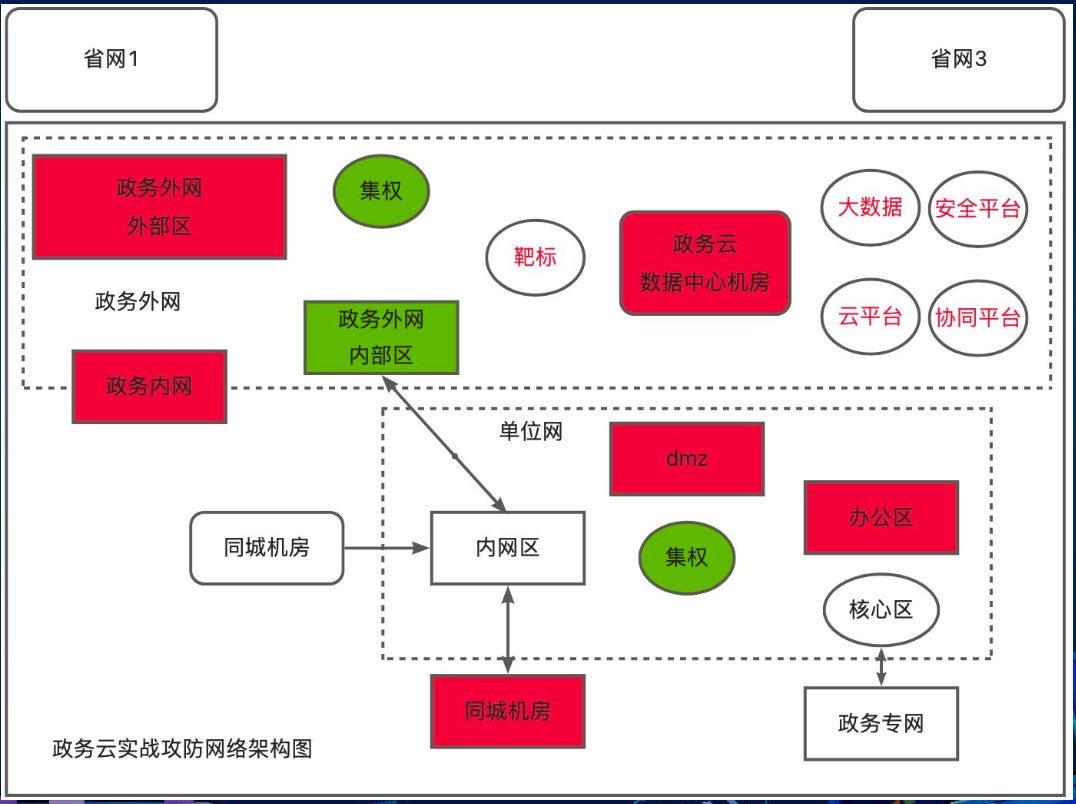
e-Government network architecture
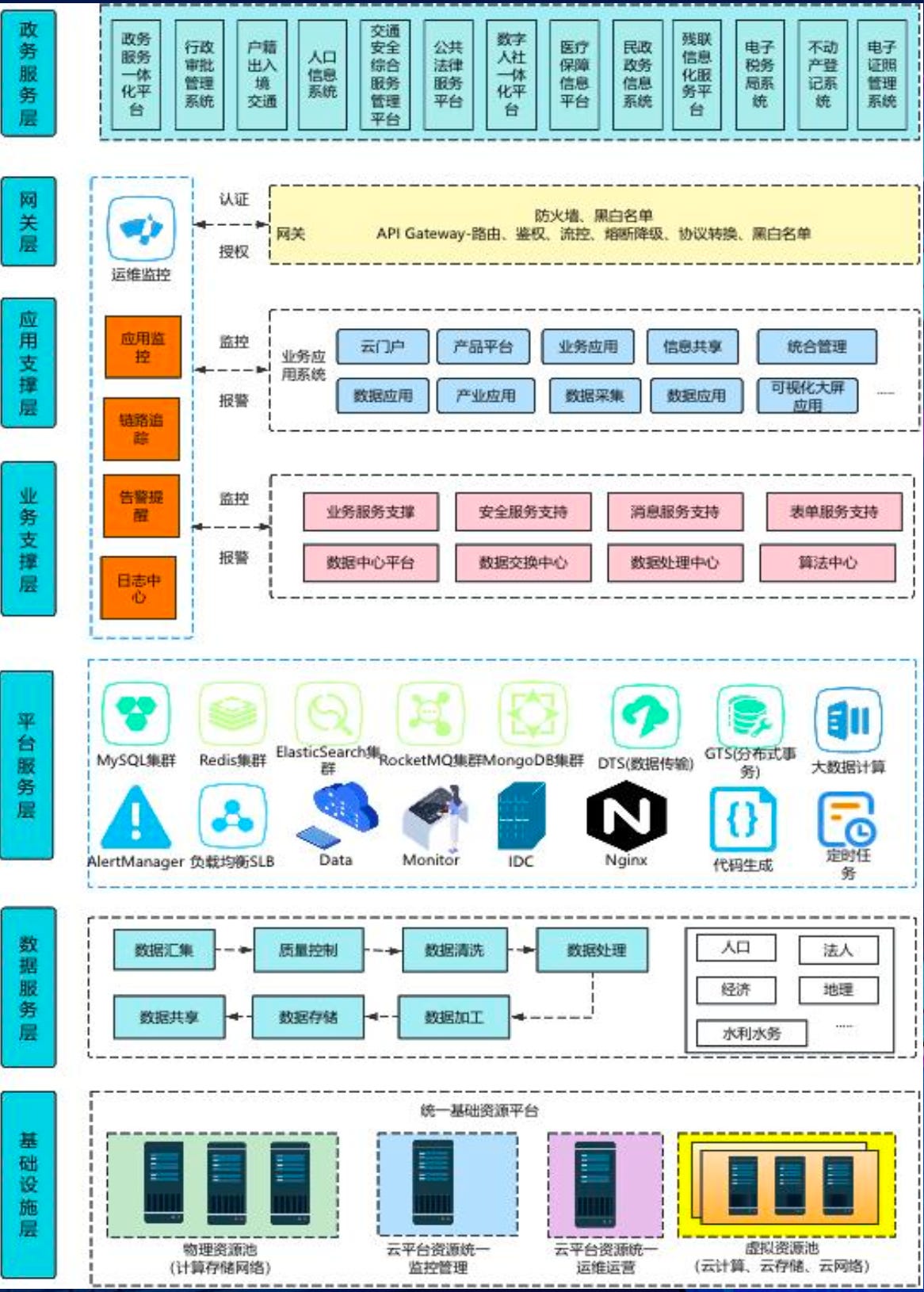
One very interesting aspect of the presentation were the structural details on China's e-government infrastructure. Not exactly classified information and often rather high-level but still interesting.
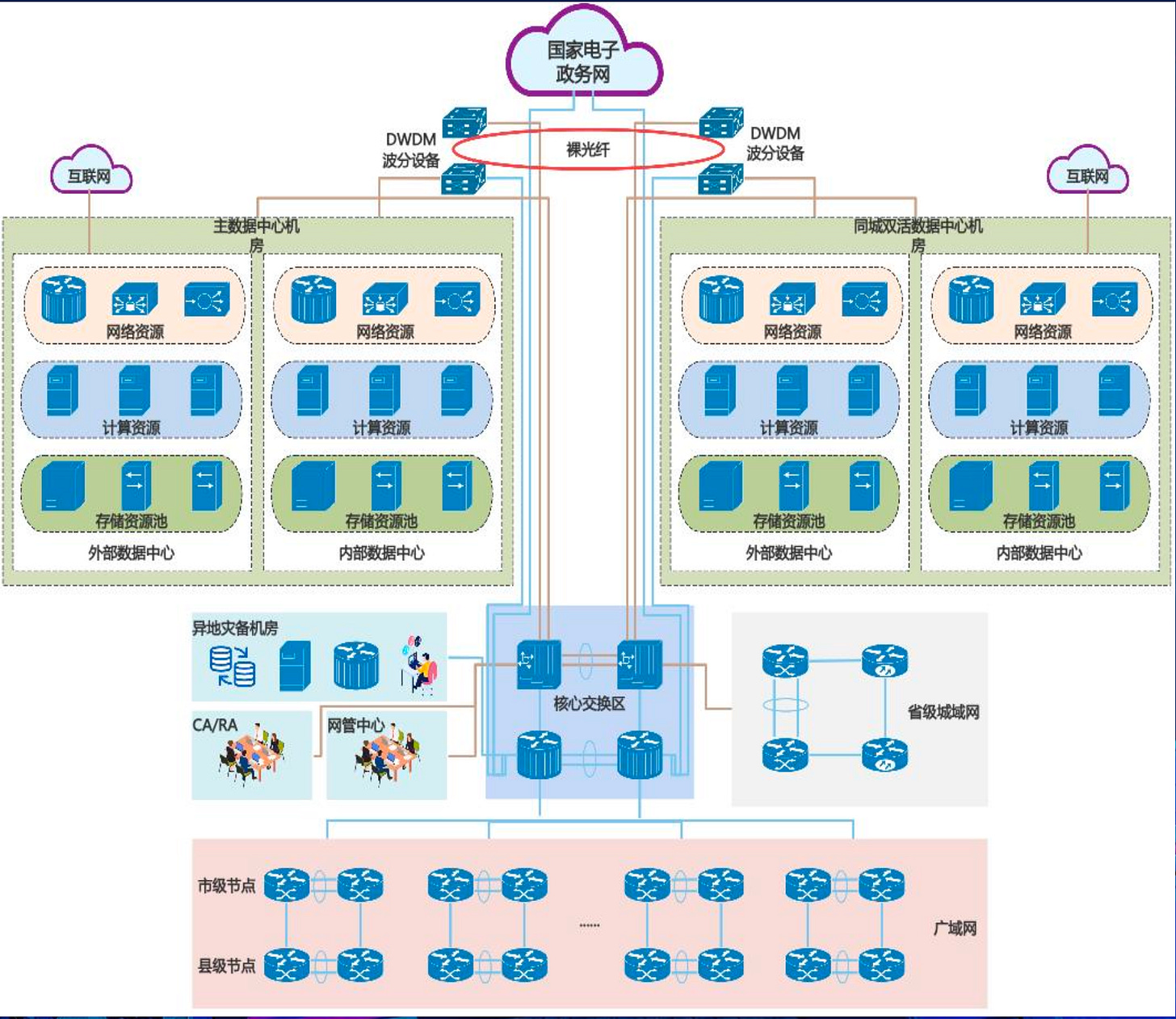
Especially as many services are increasingly getting online, so grows the attack surface. It is not only China that struggles with this challenge of course, but just by the sheer size of it paired with ‘China speed’, the threat model is significantly larger compared to to other nations at this stage (except the US maybe).
Attack scenarios
The presentation also runs the audience through a couple of example attack scenarios to show how those interconnected elements can be used to access classified and protected datasets. We would even assume these scenarios are modeled along earlier security incidents. This section aims to demonstrate the weaknesses of the overall design of current systems.
7 scenarios are given, with the more detailed ones entailing: penetration of a Bastion Host, breaching a DMZ setup and exploiting 0-day to further enter the system, and social engineering via WeChat and a malicious software package.
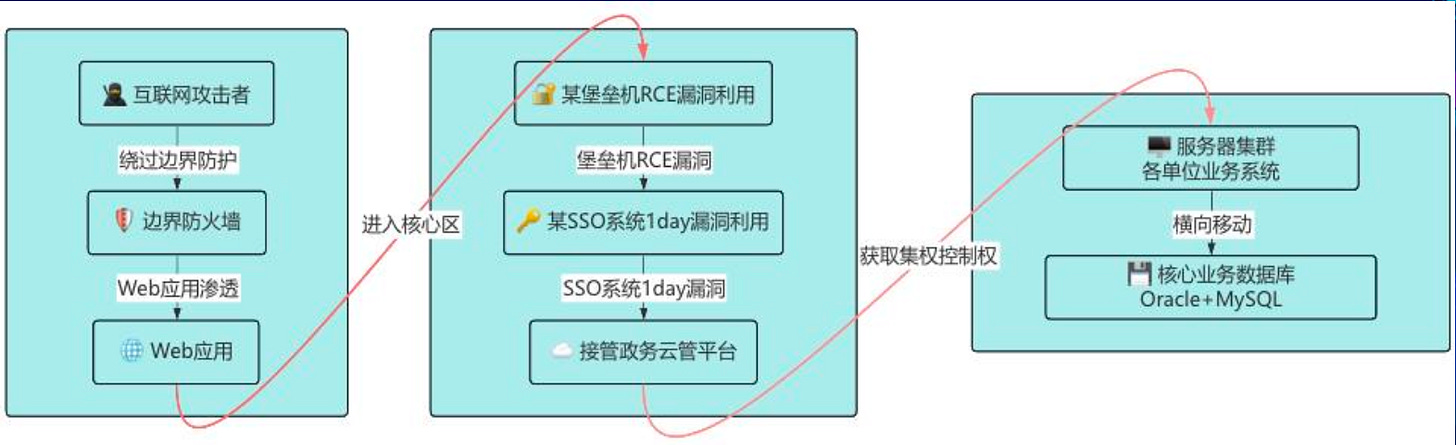
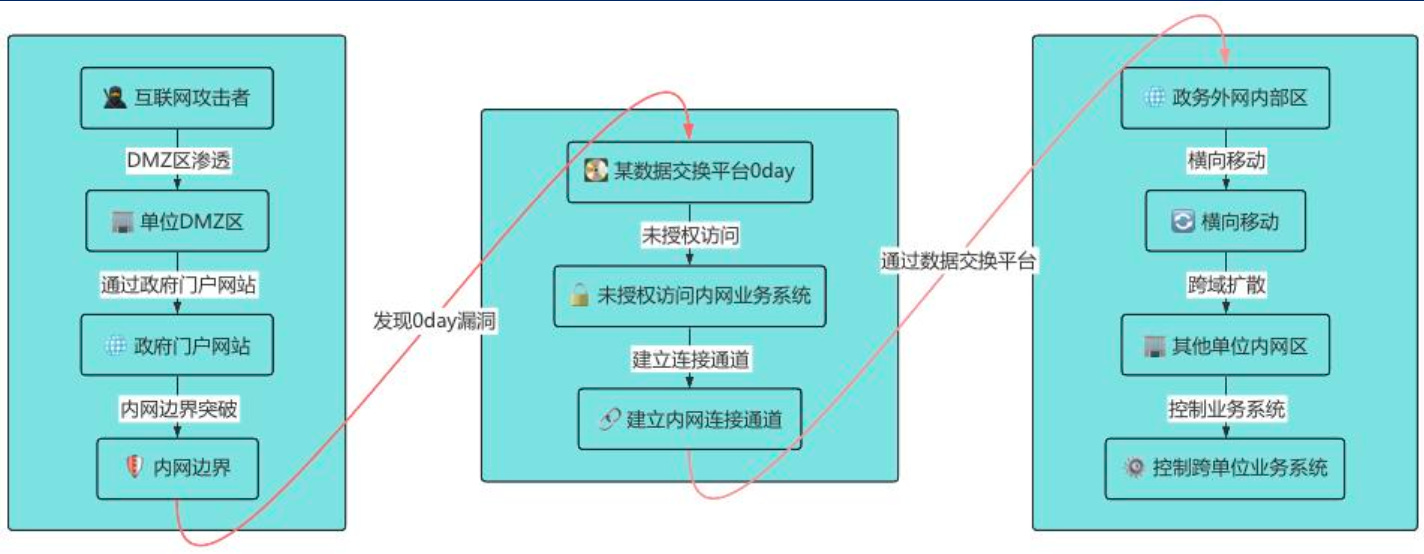
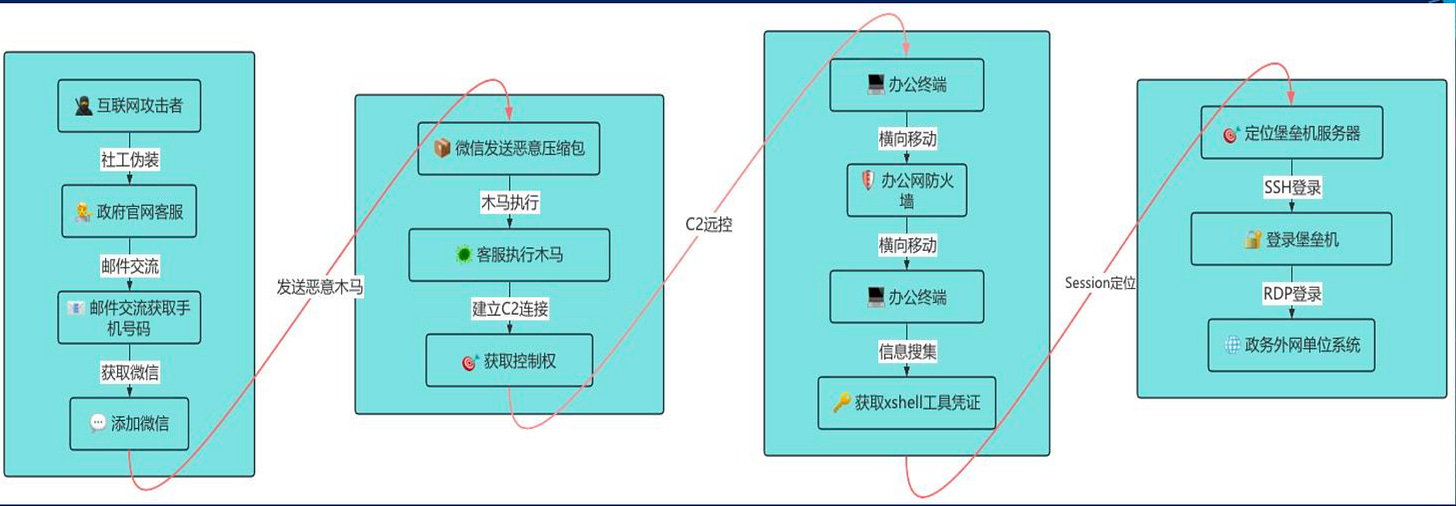
Now, we are not given any information on the potential attackers. But judging by the cases chosen, the attacks cover a wide spectrum including a mix of 0-day exploits, social engineering and critical security infrastructure penetration.
Qualifying targets
To reduce the PoCs in the future, the presenter implied that a better pro-active security audit is needed and recommended quantifiable red-team drills to discover loopholes, vulnerabilities and security lapses in this sprawling setup.
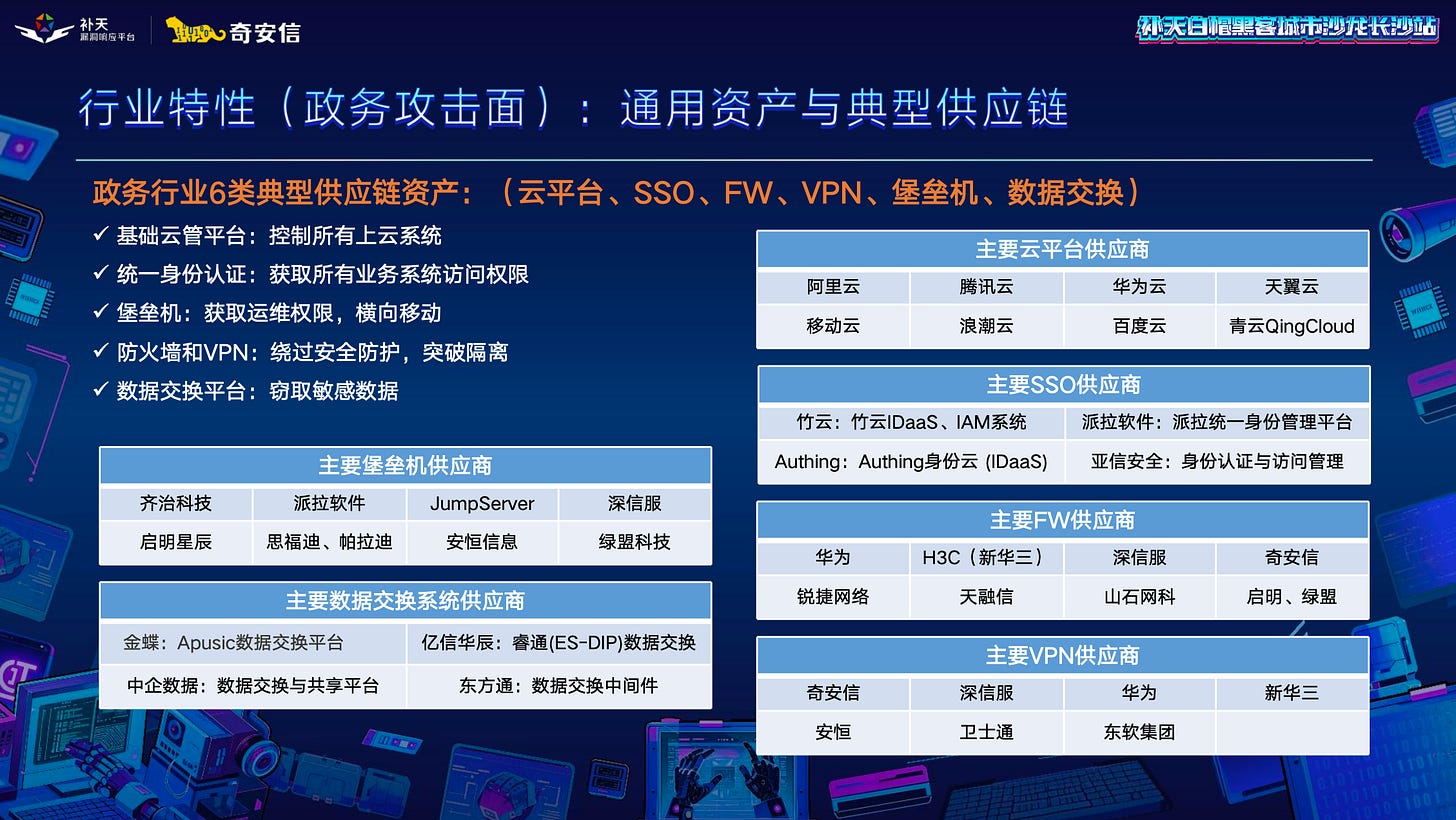
The presentation proposed a scoring system for red-team exercises to provide an easier, quantifiable way to identify issues. To identify the fields that should be at the focus of red-team security audits, the presentation took the audience through four categories: high value targets, attacking big datasets, bypassing network isolation and attacking collaborative platforms.
A. High value targets
High value (高价值目标 ) are mainly access control hubs, security operations platforms, administrative approval systems, population databases, pandemic data, government systems etc.
Medium value (中价值目标 ): Government platform mobile App back-end systems or social media accounts, finance administration and office support systems like video conferencing.
Low value ( 低价值目标 ): Government portal websites, decommissioned systems that haven't been taken down or test systems that are not completely isolated from the production environment.
The presentation says:
Target systems are typically set based on factors such as the criticality of the target, data sensitivity, and business impact.
Centralized systems: Systems that control large amounts of resources, such as bastion hosts, cloud management platforms, and single sign-on (SSO) systems.
Core data systems: Systems that store large amounts of sensitive data, such as citizen information databases, medical and health databases, and public resource trading platforms.
Critical business systems: Platforms that support core government operations, such as government collaborative office platforms and data sharing and exchange platforms.
To illustrate, the presentation named a few examples of e-government systems that would qualify as a target:
Guizhou Cloud System Platform (Guizhou Cloud Big Data Industry Development Co., Ltd.)
Jiangsu Provincial Government Cloud (Jiangsu Provincial Government Service Management Office)
Tianjin Municipal Government Cloud Platform (Tianjin Municipal Cyberspace Administration Office, Tianjin Big Data Management Center)
Anhui Provincial Government Cloud (Anhui Provincial Data Resources Administration)
Inner Mongolia Autonomous Region Government Cloud (Inner Mongolia Autonomous Region Big Data Center)
Fujian Provincial Government Cloud (Fujian Provincial Big Data Administration)
Jilin Province’s Jilin Xiangyun (Jilin Xiangyun Information Technology Co., Ltd.)
Jiangxi Provincial Government Data Sharing Platform (Jiangxi Provincial Information Center)
Shanghai Municipal Government Cloud (Shanghai Big Data Center)
Guangdong’s Digital Government (Guangdong Provincial Government Service Data Management Bureau) (Digital Guangdong Network Construction Co., Ltd.)
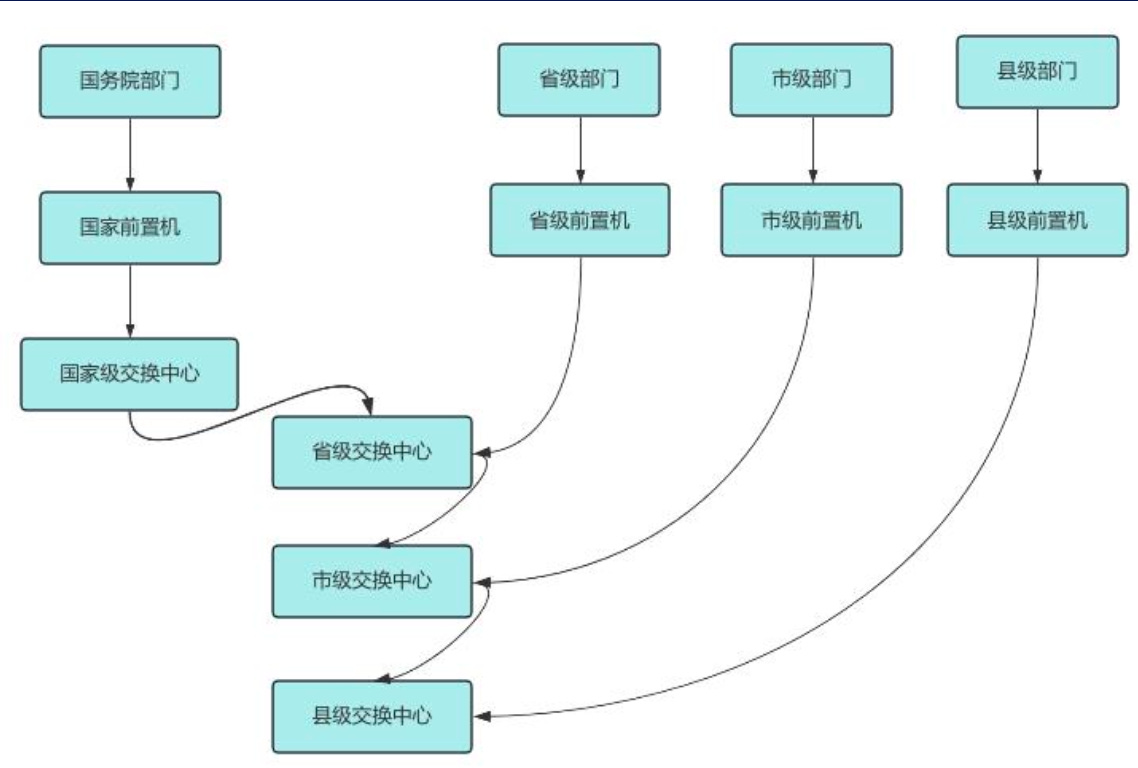
B. Attacking big data assets
According to the presenter, a red team can score major points by attacking data exchange points like public resource trading platforms or systems that process cross-departmental information, government collaboration systems (platforms central to the governments daily work that contain large amounts of internal memos, address books, and meeting minutes), and government databases involving citizens data as household registration, social security, and identity information. The document even gives us a brief overview of the data flow between national government, provincial administrations and municipalities:
C. Bypassing network isolation
This is an obvious one when looking at Figure 1 above. Here is a machine translated version of the slide's content that already pretty much sums it up:
‘Breaking through network isolation is a key strategy for scoring. The most prominent characteristic of the government service network environment is the parallel operation of multiple networks and restricted interconnection.
Typical government networks include the government extranet, government intranet, the internet, and office networks. Some industries have built dedicated networks covering the entire country (such as public security networks and medical insurance networks). These networks exist in both isolated and interconnected environments.
Types of government network isolation breakthroughs: Government extranet isolation, internet extranet isolation, intranet logical isolation, strong intranet logical isolation, targeted dedicated network isolation, cross-unit network isolation, physical intranet isolation, international public network isolation.
- Finding cross-network services: finding a server that connects to two isolated areas simultaneously (such as a dual-NIC server, VPN server, desktop cloud system).
- Exploiting firewall policy flaws: finding access policies that are temporarily open but not promptly closed.
- Establishing multi-level springboards: by continuously controlling multiple servers located in different areas, gradually infiltrating the core area.
- Implementing supply chain phishing: selecting software vendors, maintenance service providers, or website developers with relatively weak defenses, using social engineering to compromise the vendors, and then using their legitimate and trusted permissions to penetrate government targets’.
D. Attacking collaborative platforms
As the Chinese government institutions are increasingly interconnected or working via shared network resources, the presentation suggested that this attack route is another ‘profitable’ one and particularly focused on the fact that many government agencies use the vanilla or modified versions of commercial communication tools like WeChat, DingTalk to communicate with citizens and each other. The presenter suggested therefore supply chain attacks might be a plentiful bounty.
Further, this route can be used as a springboard for further social engineering attacks as access to those social media accounts operated by government entities can reveal more contacts or information from group chats.
Conclusion
Overall the presentation stayed pretty high level and didn't present a lot of actionable details. But we still can get a good sense of the dense and sprawling system architecture of Chinese e-government services. You can clearly see how it poses a daunting task for Chinese cyber defenders.
Further, it provides a fertile training ground for Chinese red-team members to sharpen their knifes and test complex attack methods that easily could be modified and transferred to genuine attack operations against foreign targets. As much of the Chinese software ecosystem is built on open source, the proficiency of Chinese red-teams exploiting them is pretty good.
Overall, the take on how to attack and penetrate such systems is quite comprehensive and although we are not given direct, technical insights on how to conduct those operations, our general analysis is that the presenter knows what he is doing.
As with every national administration, hardening internet infrastructure while still trying to provide useful services to the population is the big challenge of the 21st century for many governments.
China is no exception.