Let's build a network range (网络靶场) !
Leaked development notes from a Chinese software company collaborating with the Ministry of Public Security in China reveals internal designs of a "network range".
The rising investment and proliferation of “network shooting ranges” with Chinese state security organs have been extensively covered by Natto Thoughts, NetAskari and many other researchers and outlets.
The point of these virtual training grounds is to provide cyber operatives a testing environment for complex offensive and defensive scenarios via simulated scenarios which are as close to the “real deal” as possible. Here cyber security operatives can run and test malicious software in a secure Eco-system to study its behavior or tweak the functionality. But overall we know relatively little about the internal designs of those setups in China.
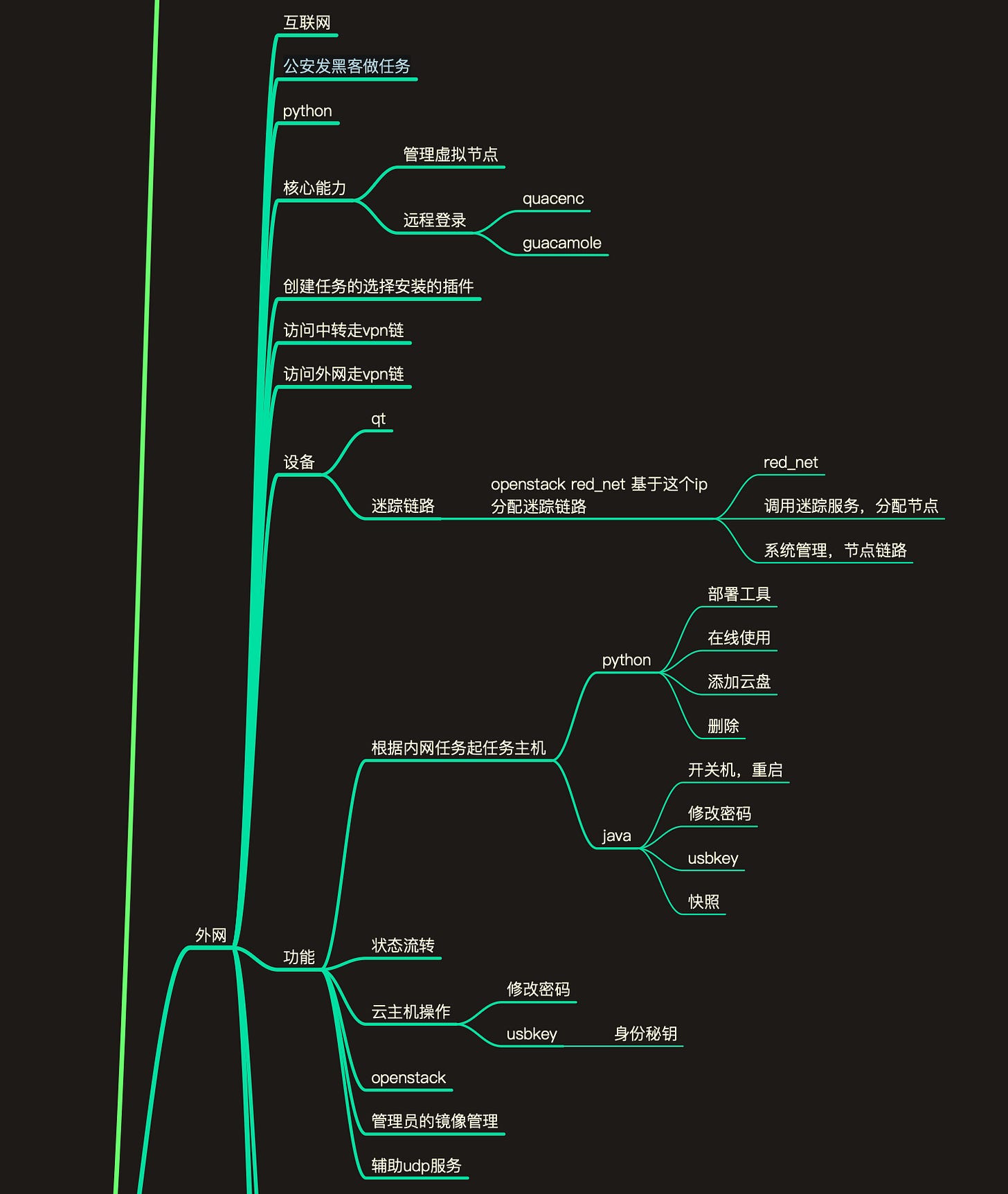
A leaked “mindnode" map from the device of a software developer working for the company Nanjing Saining Information Technology Co. in China gives us a slight glimpse into some elements of the system design.
The enterprise, also known as “Cyber Peace”, has been a provider of software solutions for the Chinese government for quite a while. Founded in 2013 its initial staffing was made up of former members of the famous Blue Lotus Team from the elite Tsinghua University in Beijing.
Offering a wide range of general software products for private and public entities, their cooperation with the Chinese state on cyber security matters is well documented.
The data leak also includes a contact sheet of members of the R&D Department of the Public Security Department in Nanjing who presumably were involved in helping with the requirements.
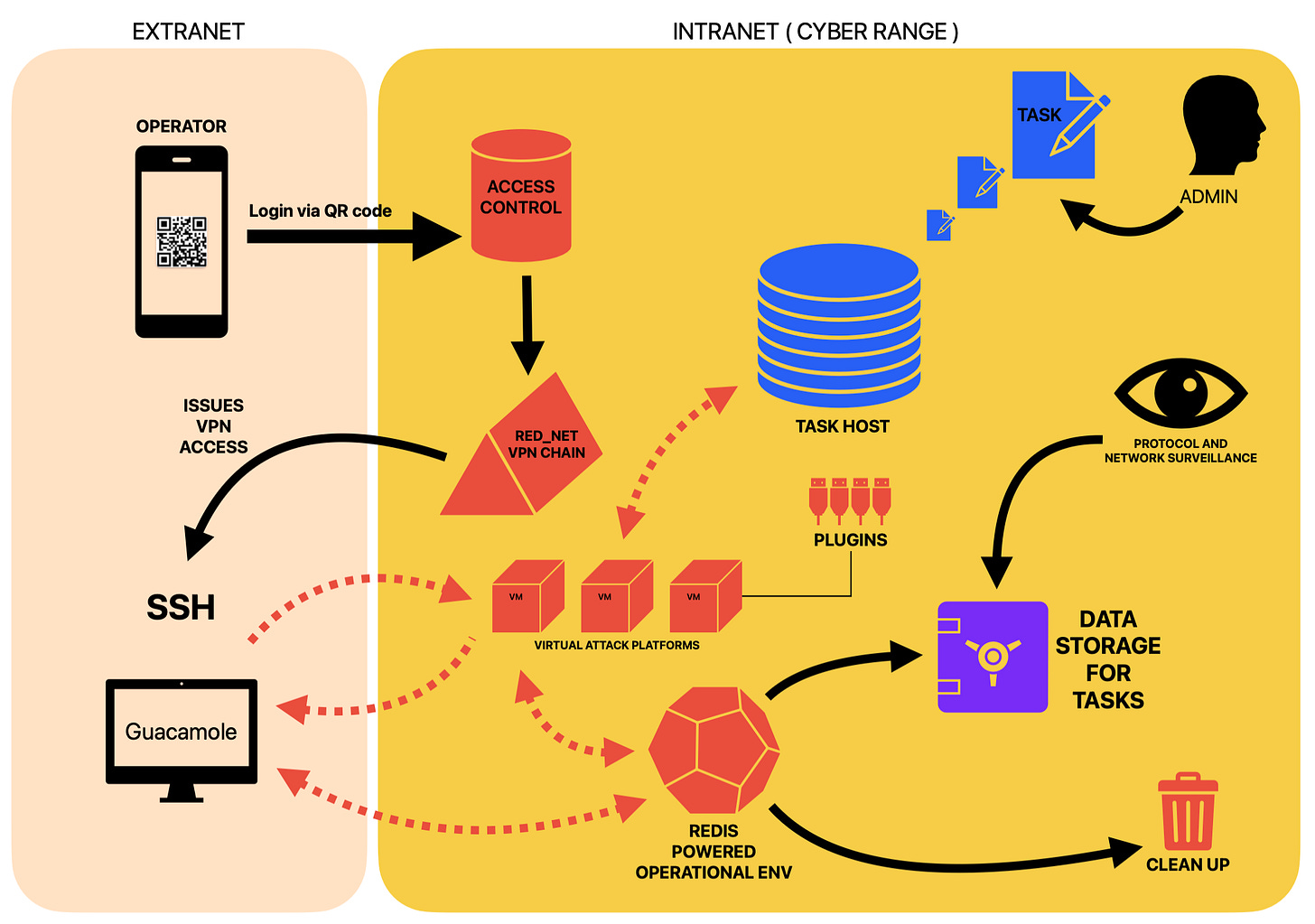
Here is a simplified diagram of how this cyber range is organized according to our understanding of the “mindnode” and how similar systems are designed:
Disclaimer: The following analysis is entirely based on what we can find in this document. Of course that has its limitations as this “mindnode" is just production and developer notes. This is not a detailed explanation of how the system works or a complete technical manual.
Tasks and Task Host: This is the operational core of the system. An administrator inside the cyber range is defining tasks which are used to build a “task host”. This seems to be the simulated attack environment the operators eventually will try to breach. A USB key driven authentication for administrators seems to be possible. Each task is given an ID so it can be traced in further operations. The admin can restart hosts, kill them or change their characteristics.
Operator access: All operators seem to gain access to the system from outside via a QR code driven access control. On successful authentication, they are receiving a VPN link to the cyber range environment ( here specified as “red_net”), as they are located outside the cyber range. This VPN service is most likely hardware driven on the side of the cyber range. A Guacamole powered dashboard is the main point of access for the operator, but SSH is possible according to the document.
Virtual Attack Platforms: After an operator is authenticated and logged in, he/she can setup Virtual Machines for its “combat missions”. This systems probably operate on Linux and are the operational stepping stones to conduct cyber security operations against the "Task Host”. The user can expand the VM’s functionalities with a plugin infrastructure. These VM’s can receive data from the operator via SFTP, web upload etc.
Technical observations: The full system seems to make heavy use of OpenStack for running the internal network structure. Redis databases is also heavily integrated. Many of the automated tasks seem to have an Python API or rely on JAVA. Remote login is managed via Guacamole. All the activities of the operators and the activities of the “combat mission” VMs are monitored, most likely for after action reports and analysis. There is also the mention of an “optical gate” (光闸), implying that the internal hardware relies on fiber optics. But how that plays into the whole setup, is hard to say.
What is interesting, is that this modular mission oriented VM deployment to conduct “offensive operations” seem to echo the certain aspects of the "Hawk Eye” framework we have written about here:
Summary
A lot of questions still stay unanswered and without a detailed technical manual it is very hard to say with certainty that this is a cyber range instead of lets say a “combat platform” that the Ministry of Public Security uses to actively hack targets ( see below for clarification ).
There is the mention of “公安发⿊客做任务" which translates roughly to : “Public Security sends hackers to do tasks”. That of course could hint towards a stronger role in cyber offensive operations. But we just miss too much context.
As Nanjing Saining Information Technology has been documented to be heavily involved in Cyber Range design before, we would therefore rather put this project into this category. A lot of technical observations seem to fit the requirements as well. But that said, dual-use is one of the strengths of the Chinese state security organs. The developer who created the mindnode map also describes himself as an expert for "cyber range” design on his CV.
The project description seems to be from around 2021, so most likely, similar projects might have expanded much further and be more proficient by now. Nonetheless, we found it interesting to get the perspective of an developer that has to work on such tools, which in its core is just another cloud platform so to speak.
What we found interesting is the heavy use of open source components like OpenStack or Redis, making the product probably a far less expensive affair than many internationally marketed products.
China's cyber security landscape, especially when it is connected to government security agencies can be quite opaque. Every little snippet of information sheds some more light on the bigger picture.
EDIT - 20 October 2025: With more information now, we can say, that this is a cyber-range to train operatives in cyber offense and defense. Here are new documents that we could get access to that clarifies the "training” aspect of it all.




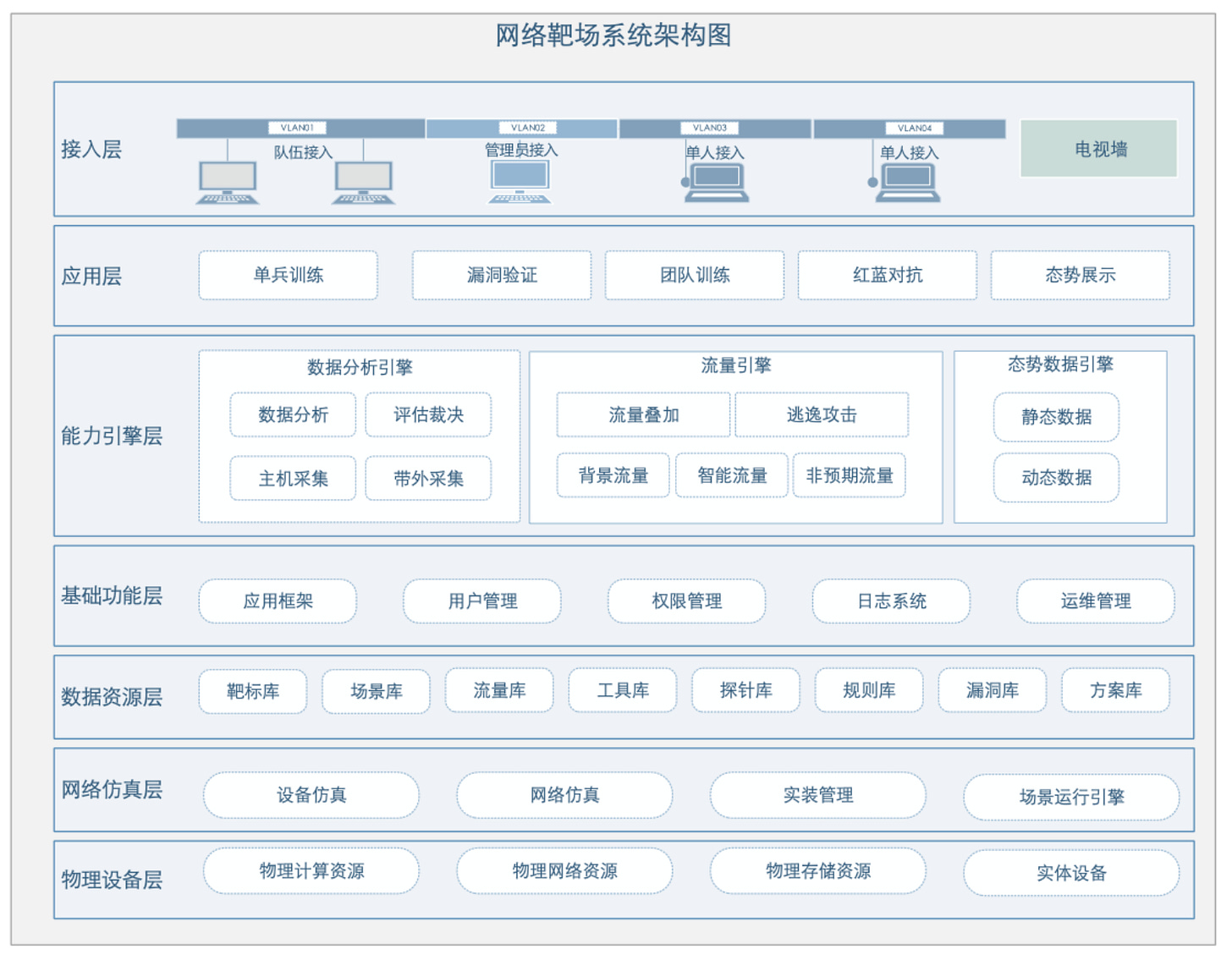
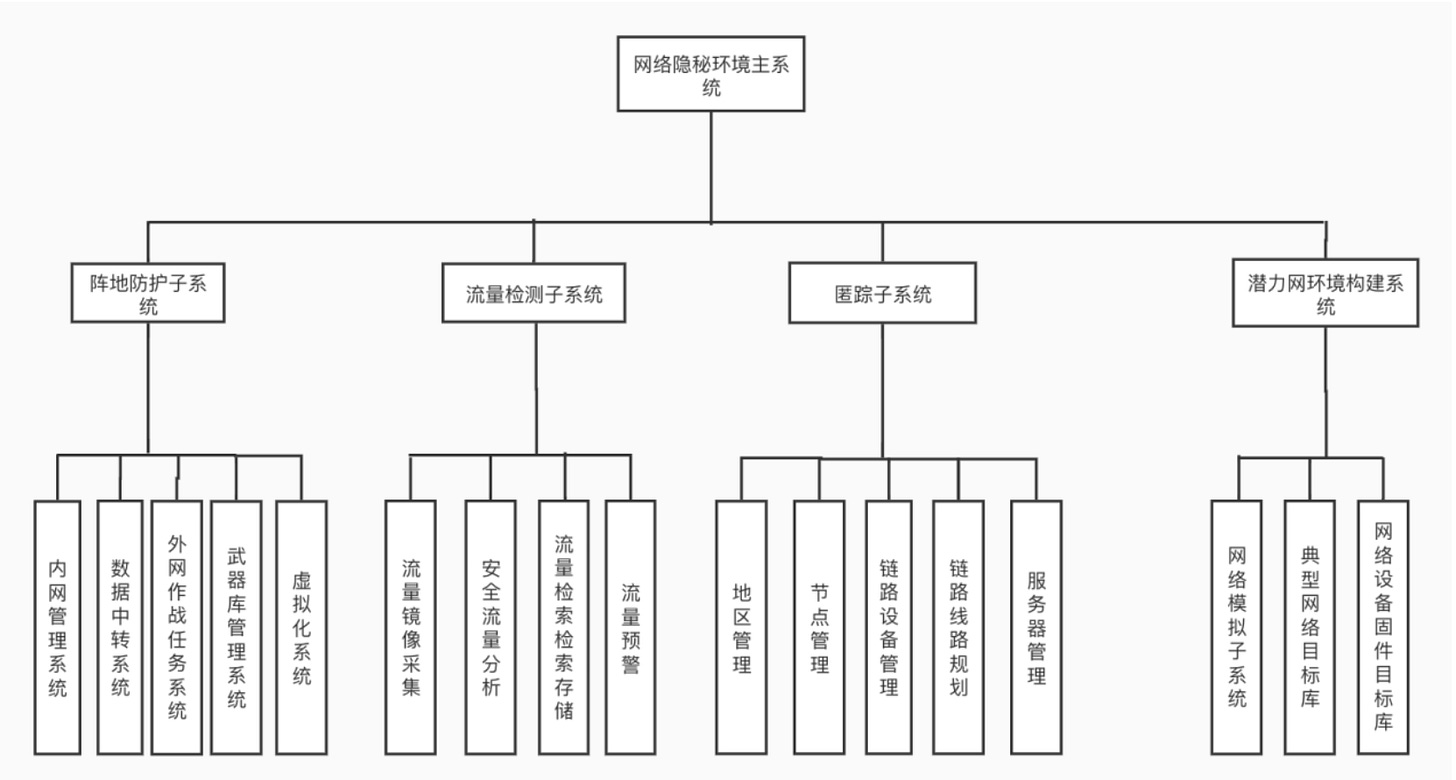
“Nanjing Saining Information Technology Co., Ltd” who’s initial founders are linked to Tsinghua University's infamous Blue Lotus Team. Just another example of how the CTF culture grooms talent.