What's in the box !?
NetAskari got access to a little "toolbox" of a Chinese red-team/pen-tester. Let's explore.
China’s sprawling cybersecurity landscape has been extensively documented over the past years. Since the revelation of the I-Soon leaks (and others that followed), it has become increasingly clear that parts of this private, commercial sector have at times moonlighted as cyber strike operations on behalf of the Chinese government.
Traditionally rather closed off from the rest of the world, the country’s red-team and pen-testing community is often shrouded in mystery. This is especially true as many Chinese red teams have largely stopped participating in international hackathons since 2018. Occasional (and often incomplete) reports from national CTF events, workshops, or misconfigured online infrastructure are frequently the only glimpses outsiders get into this world. Open and frank conversations—even anonymous ones—are not always easy, as we have learned.
But this time, luck was on our side: we were able to obtain a set of pen-testing tools from an active pen-tester and security analyst in China.
As offensive and defensive security work in China are at times so closely interlinked, we thought it might be interesting to take a closer look at the tools used by professionals engaged in exploit hunting.
We are not suggesting, of course, that these software packages are explicitly used by APTs or sophisticated state-backed hackers in China. Rather, they offer a small but useful overview of what the “foot soldiers” might bring to the table.
If you are a seasoned pen-testing professional, it is unlikely that anything here will feel new or revelatory. If you are expecting a brand-new, deep insight into Chinese APT tooling, you will be disappointed. But if you are up for a modest and interesting exploration, come along.
BURP is king
Using the popular penetration testing and security tool Burp by PortSwigger seems as much liked by Chinese pen-testers as it is by colleagues across the world. Probably not a massive surprise as the software suite is pretty solid and considered a “standard” for exploit hunting of web applications for years. But more interestingly are the collection of Chinese made plugins and extensions that we can find in this collection :
ByPassPro - based on AutoBypass403 it is an automated permission by pass tool) [>]
Domain Hunter Pro - target information management integration for Burp [>]
MingDong - older but extensive collection burp suite plugins and also a localized Burp suite in Mandarin. It also provides a pen-testing questionnaire. [>]
OneScan - plugin for recursive directory scanning, discontinued since June 2025 it seems. [>]
Turbo-intruder - complementary plugin to Burp Intruder by PortSwigger, to send large numbers of HTTP requests and analyzing the results, discontinued in 2020. [>]
xia_yue - some http privilege escalation automation tool. [>]
xia_sql - SQL injection. [>]
TsojanScan - extended vulnerability detection plugin by the Chinese team TsojanScanTeam. [>]
Overall, a lot of these plugins are pretty common ware and often just encapsulating known techniques and exploit pattern. But I guess the Chinese market needs its own variants.
The “Chinese” tools
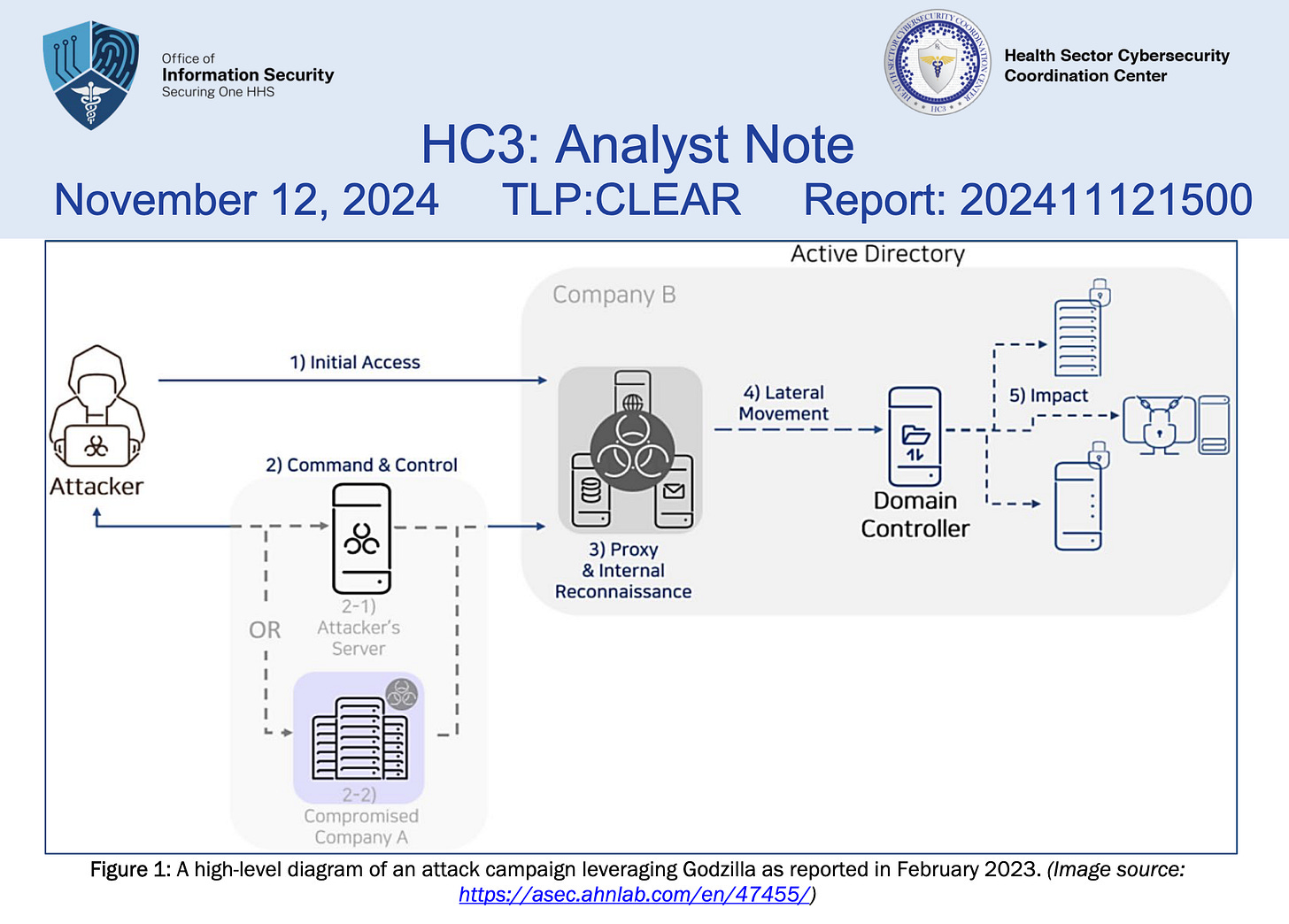
One more interesting find was a copy of Godzilla. A webshell / exploit framework that has been used in a series of attacks in 2021 on US infrastructure and was on the radar of CISA and DHS. The “Health Sector Cybersecurity Coordination Center” released a more detailed analysis of the tool in 2024.
It states:
Godzilla was created in response to existing webshells that are often detected in attacks; Godzilla avoids detection by using Advanced Encryption Standard encryption for its network traffic, which makes it more difficult to detect. Godzilla is considered highly capable and full of functionality.
It is officially attributed to actors associated with the Chinese state, though it is publicly available and therefore accessible to everyone. I guess you can’t draw too many conclusion from that circumstance except that it is a rather capable tool aimed at Chinese pen-testers.
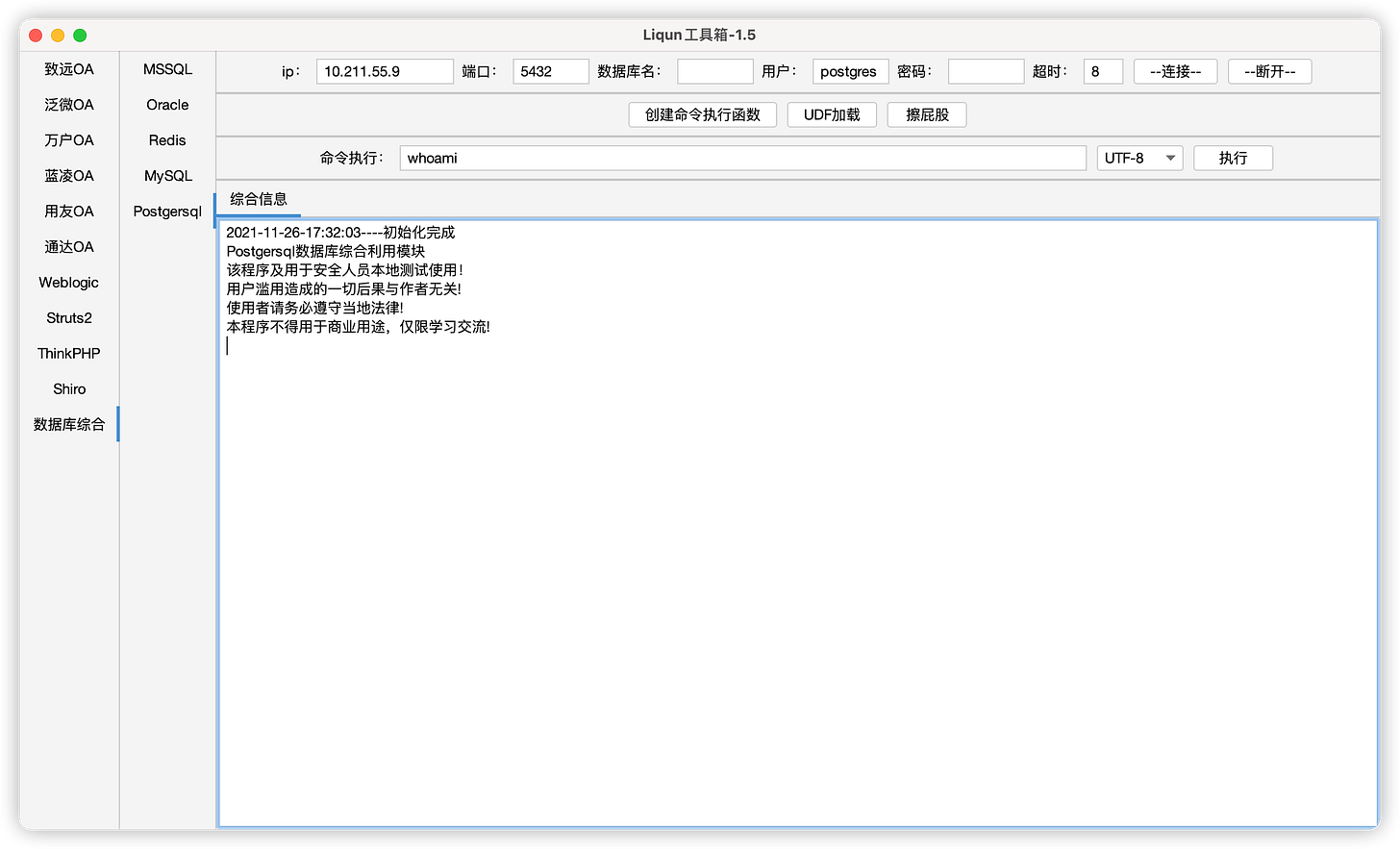
Then there is a copy of LiqunKit. Another Chinese language exploit framework that had its last major overhaul around 2021 and focuses on exploits of MySQL, Oracle, Redis, PostgreSQL, Struts, Weblogic etc. and some Office Automation vulnerabilities.
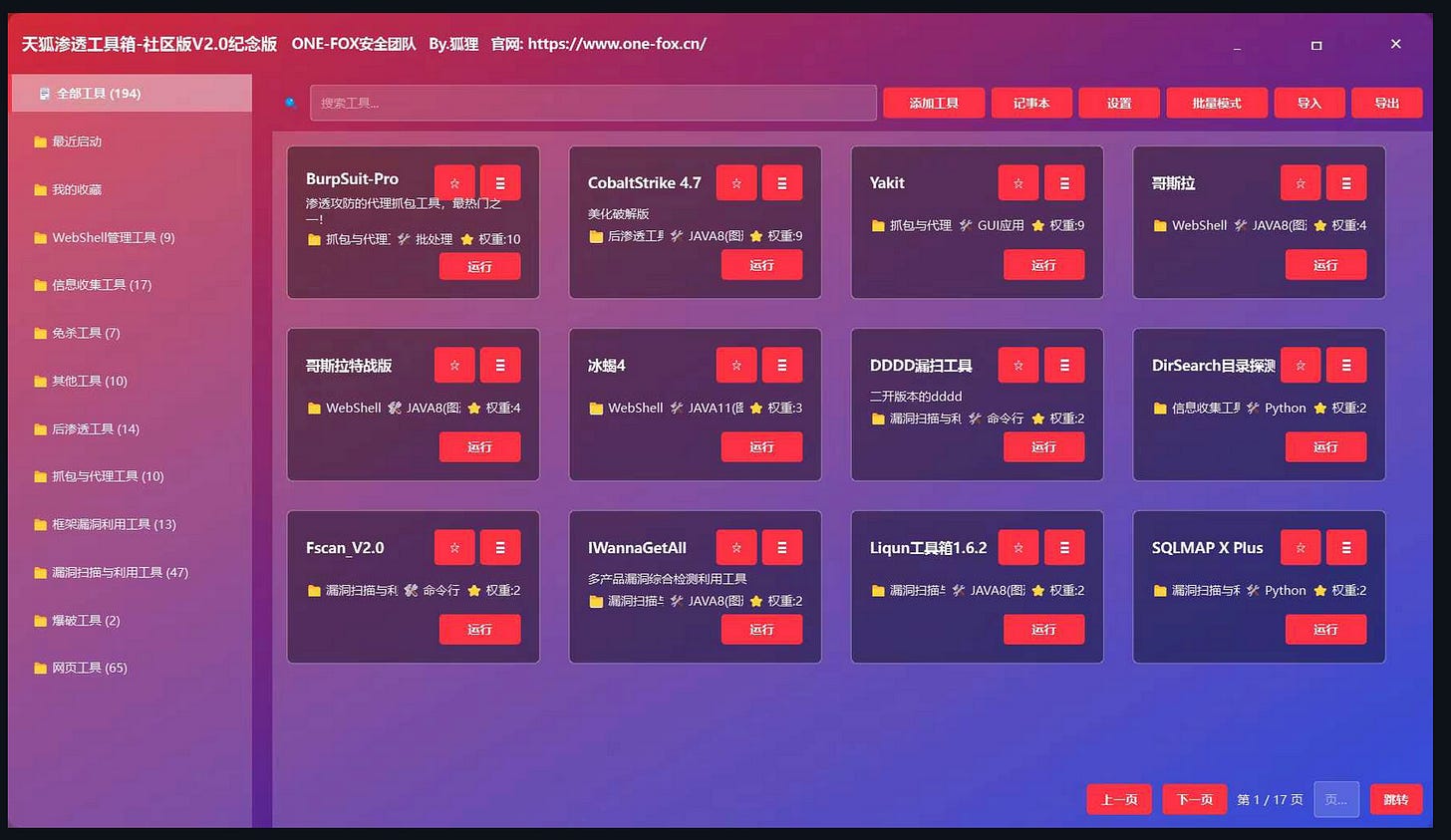
A full copy of 天狐渗透工具箱-社区版V2.0纪念版 is also available in the repo. This is a rather comprehensive, commercial exploit Meta-framework from that doesn’t seem to focus on payloads or specific exploits but provides some control center for more well known exploit frameworks like Cobalt Strike, Burp etc.
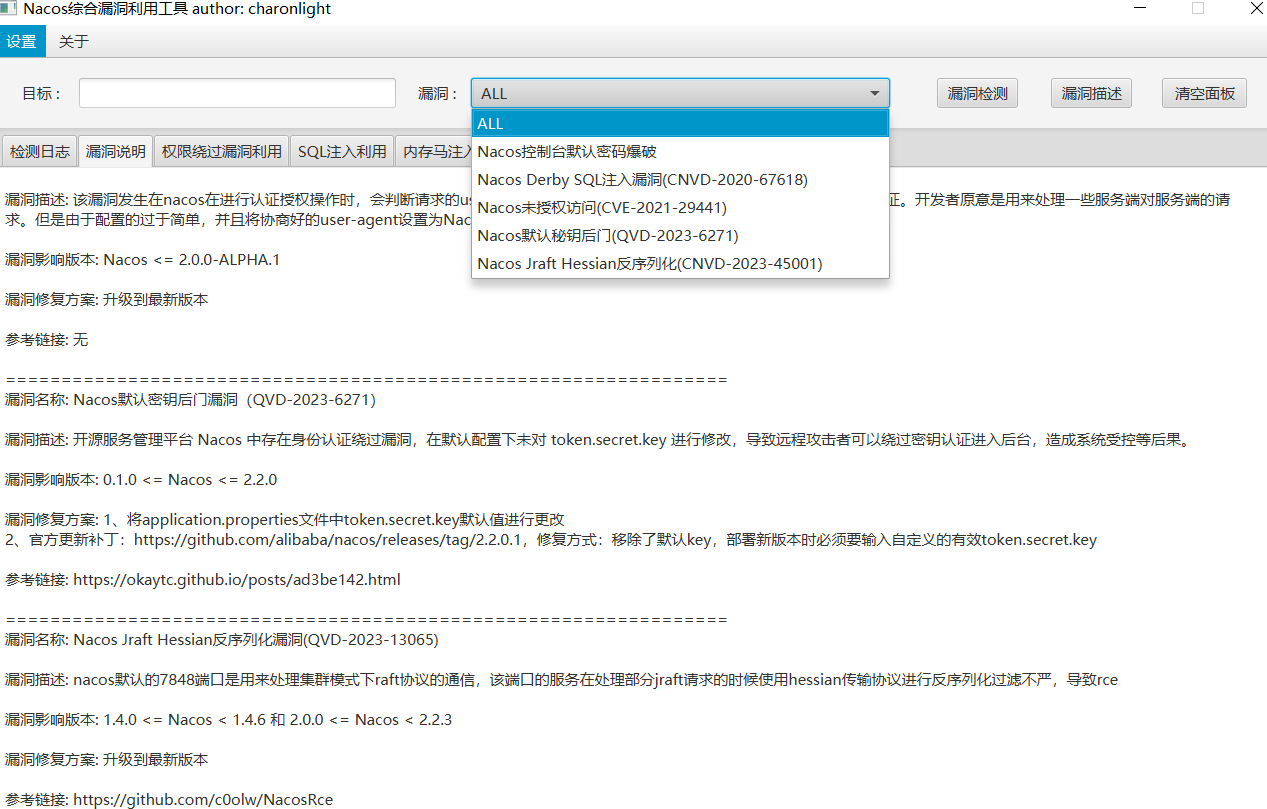
Finally we can find a version of NacosExploitGUI, a exploit framework for the Alibaba NACOS web (micro) service management platform. Not massively surprising as AliBaba cloud and its side products are very wide spread in China ( and adjacent countries ). The Github pages for NacosExploitGUI describe it as:
vulnerability exploitation GUI tool integrates the detection and exploitation of default password vulnerabilities, SQL injection vulnerabilities, authentication bypass vulnerabilities, and deserialization vulnerabilities.
Custom python scripts
When it comes to custom made tools and scripts, there is very little in the collection we could obtain. Only two python scripts do exist: python.py and sql.py.
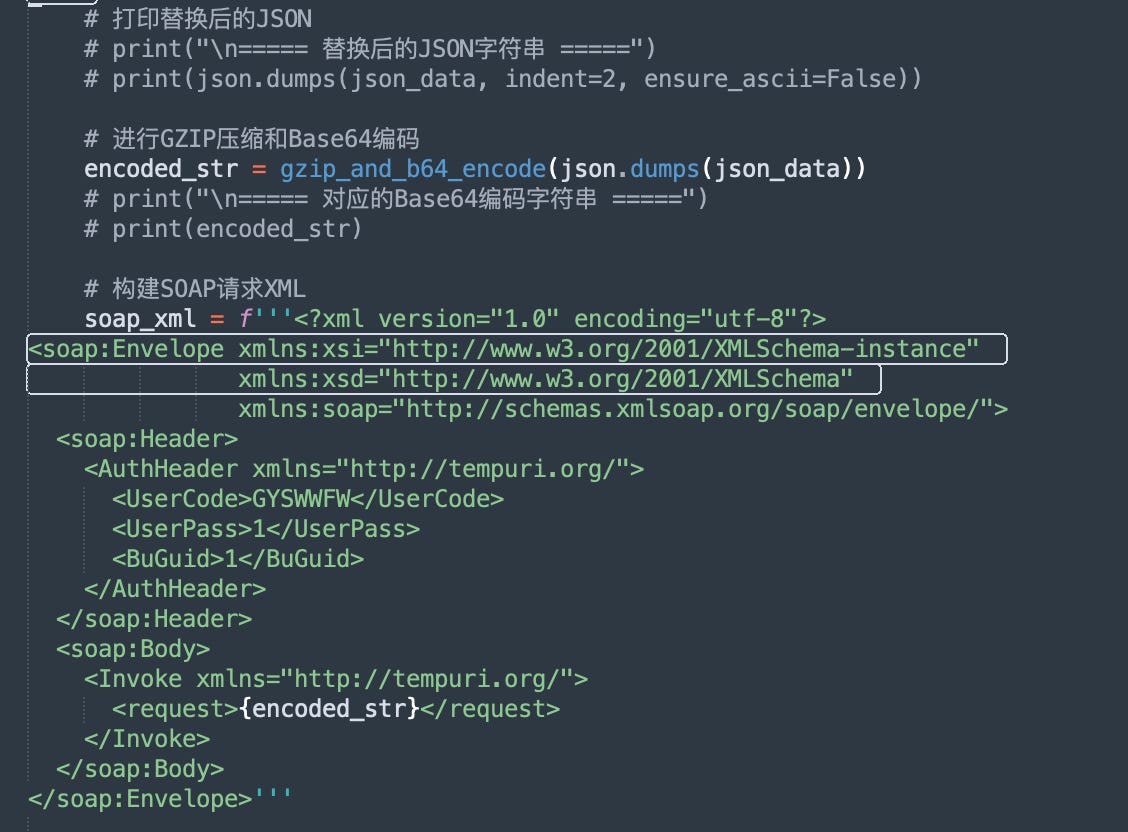
The first one is a simple http based file server that is used to provide an easy option to quickly download files from a host while the second one, sql.py, wraps SQL requests in SOAP command packages and sends it to a specific domain. Most likely to run SQL injection exploits.
Fruit of the labor
Now, having the tools is one thing, but how good are the results you can achieve with them is another. Good for us, we also got a security test report of the same operator, running vulnerability tests on some infrastructure. The report document is very incomplete, most likely a work-in-progress as of the time we received the files.
We can't of course go into the details here but a few examples can be presented from the WIP pen-test report :
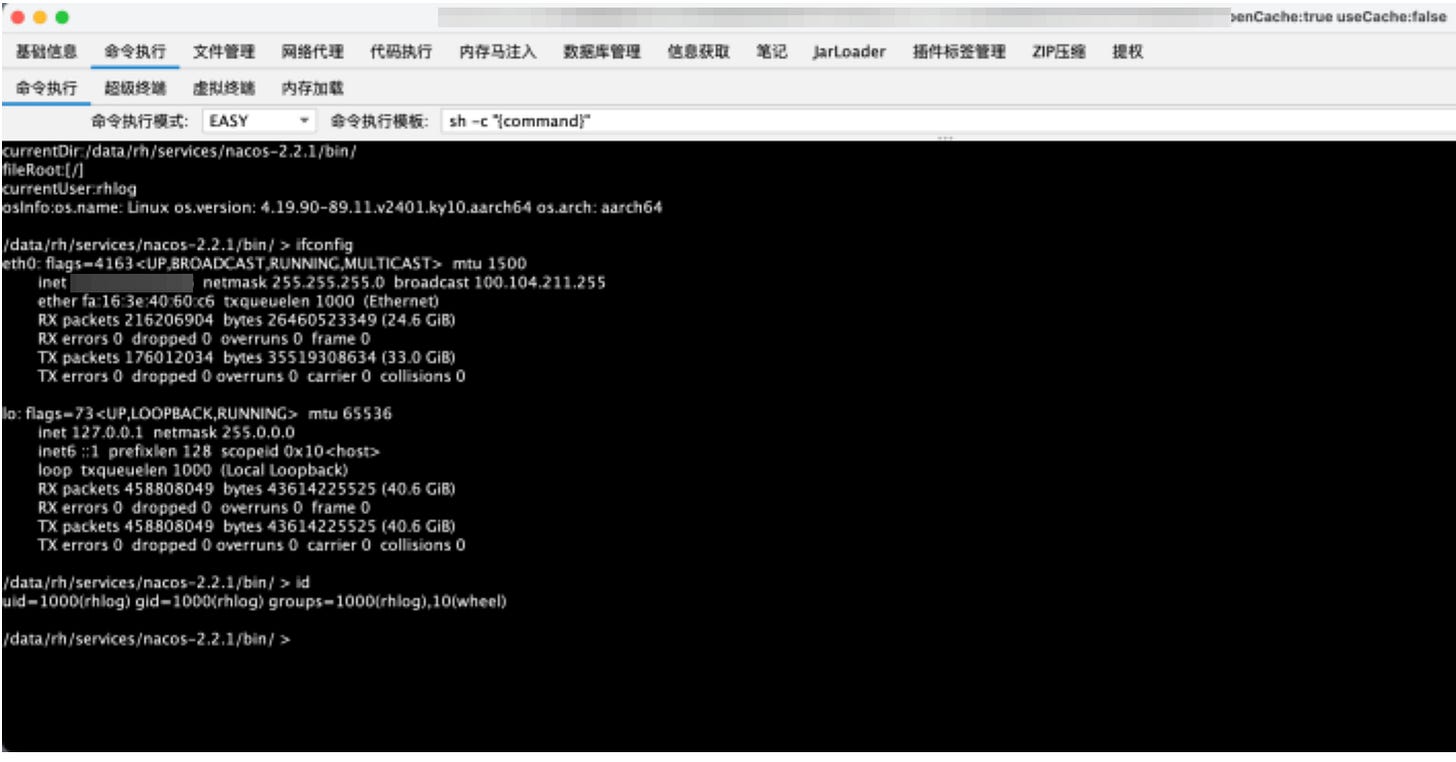
A Nacos entity exploit to obtain a Webshell.
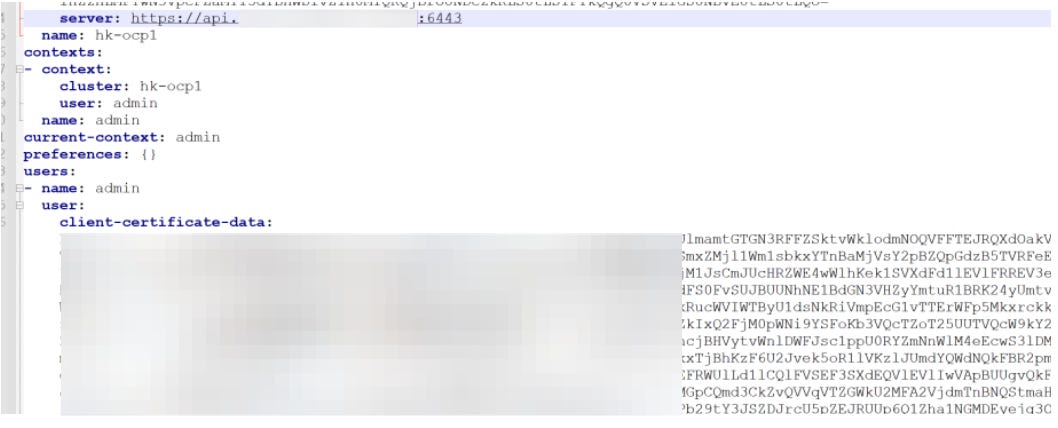
Accessing a Kubernetes cluster by obtaining admin configuration file ( the dataset also has a complete Kubernetes configuration dump, so I guess it was successful ).
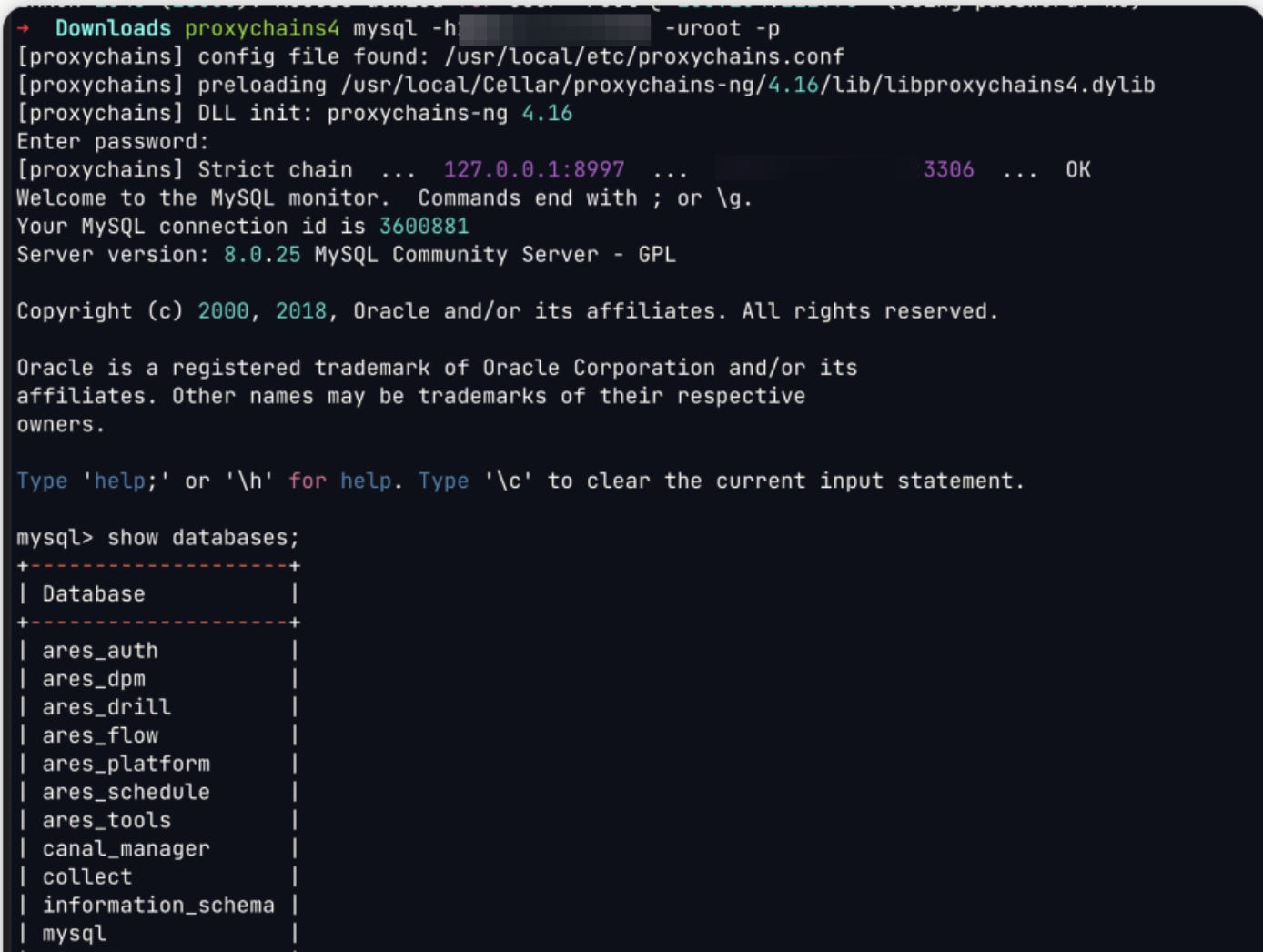
Database privilege via SQL injection through exploiting Nacos.
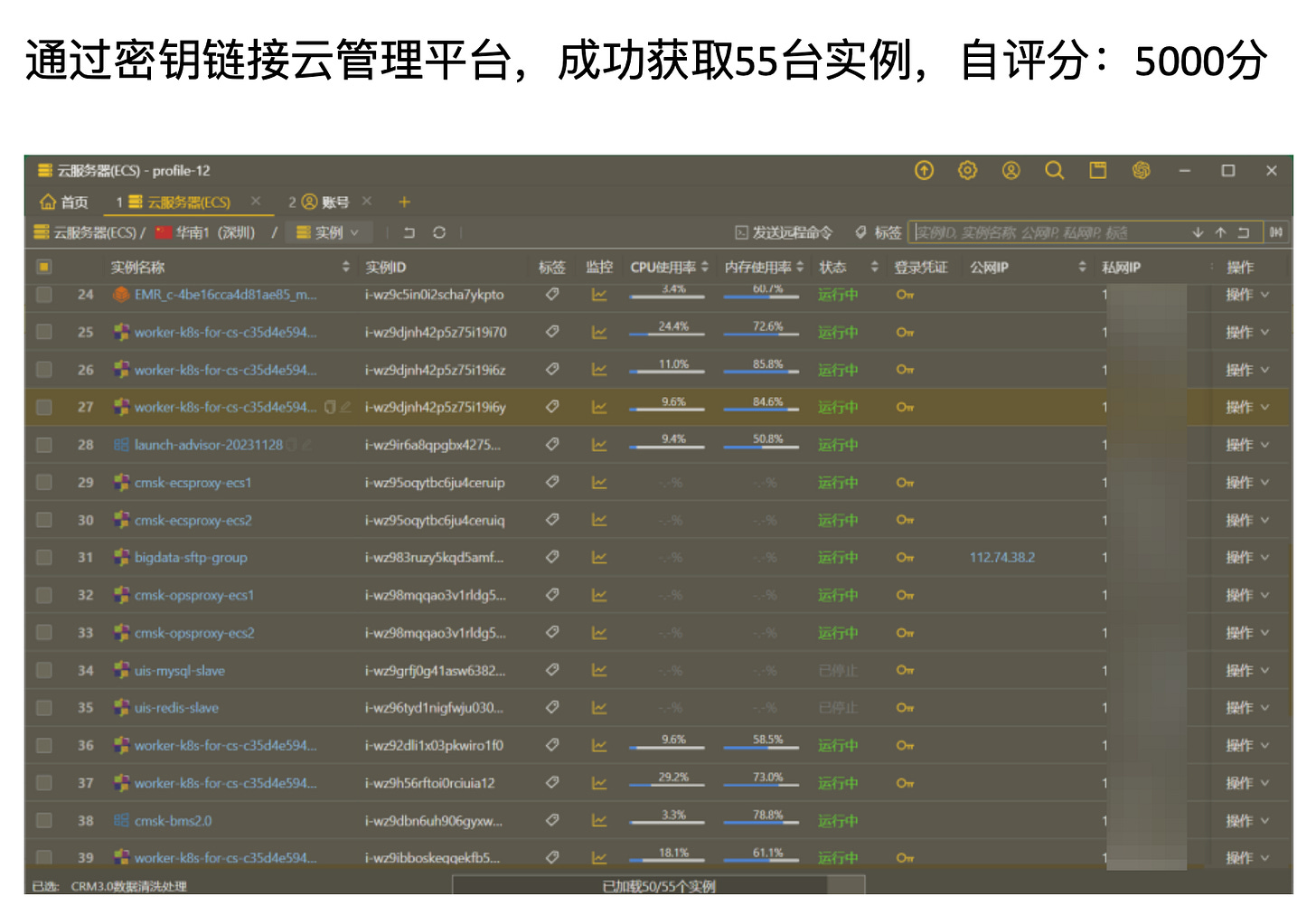
Obtaining 55 cloud server instances on Alibaba cloud, via Access/Secret Key leak, plus OSS ( alibaba cloud object storage ) access.
Final thoughts
Again, we want to mention that this individual is most likely a commercial pen-tester and we have no evidence or signs to assume that the person is working for the Chinese state or is affiliated in any way in APT activity.
So what does all this tell us ? Does it deliver any deeper insights ? Does it reveal the internal secrets of Chinese APTs ? Does it show that Chinese cyber security operatives are 1000 feet tall ? No, of course not, silly. In the end, this is just a normal pen-tester as we can find him all over the world.
For us it is more of an interesting ex-course into the world of Chinese pen-testing applications and work patterns. Maybe you found it interesting too.


Really fascinating how the tool ecosystem reflects regional infrastructure patterns. That bit about Alibaba Nacos-specific exploits being standard in Chinese pen-test kits makes total sense when you think about market penetration, but I'd never considered how much regional cloud dominance shapes the exploit landscape itself. I used to think these toolkits would converge globally with maybe some localization, turns out the entire foundation is diferent when the target environments are fundamentaly different. Also intersting that Burp is still king regardless of geography.