Critical strike: China's hacking training grounds (PART 1)
Exclusive internal design documents reveal details of China's digital training grounds, set up to attack critical infrastructure of its "major adversaries".
China’s state-backed hackers have intensified their attacks on the critical infrastructure of other nations in recent years—often with notable success. Their techniques are highly sophisticated, but just as significant is the support ecosystem that enables them to develop and refine those attacks. Hidden “digital shooting ranges” allow operatives to practice and sharpen their skills out of sight from their adversaries. Proofing their skill sets for digital warfare. Now, for the first time, leaked internal documents offer a clear view into one of these secretive virtual training grounds.
A few weeks ago, we published a preliminary analysis of a leaked MindNode map from Nanjing Saining Network Technologies, also known under its official English name “Cyberpeace” ( www.cyberpeace.cn). An established Chinese cyber security provider, closely linked to government security institutions. You can read up more on the company in a ‘Natto Thoughts’ article here.
The previous data outlined the planning and design considerations for what they call a “network” or “cyber range”. At the time, the information was rather limited, and we had to rely on a number of informed guesses to connect the dots.
Now, we have far more material to work with. And it takes us down a much deeper, and far more revealing rabbit hole. We found more detailed files on the network topology, internal communication with the client, work reports and some source code. Dating back to 2021.
The brief
One important new document we secured is the “brief”, the requirements for a system to be built by Cyberpeace. We identified the client as the Ministry of Public Security. Notably, the brief has no letterhead, insignia, or signature. The pages were photographed from a physical paper copy rather than provided as an official digital file. The whole project seems to carry the rather generic name “Expedition Cloud” ( 远征云 ).
Still, when you read through the document, it becomes increasingly clear that our initial assessment in the earlier post - that the “client” is the Ministry of Public Security - fits remarkably well ( there are more references in the dataset to the "公安”, including a contact list of members of one of it's R&D departments with their names, phone numbers, department names and other personal information ).
I’ll go through each page with a quick summary and highlight the most interesting details.
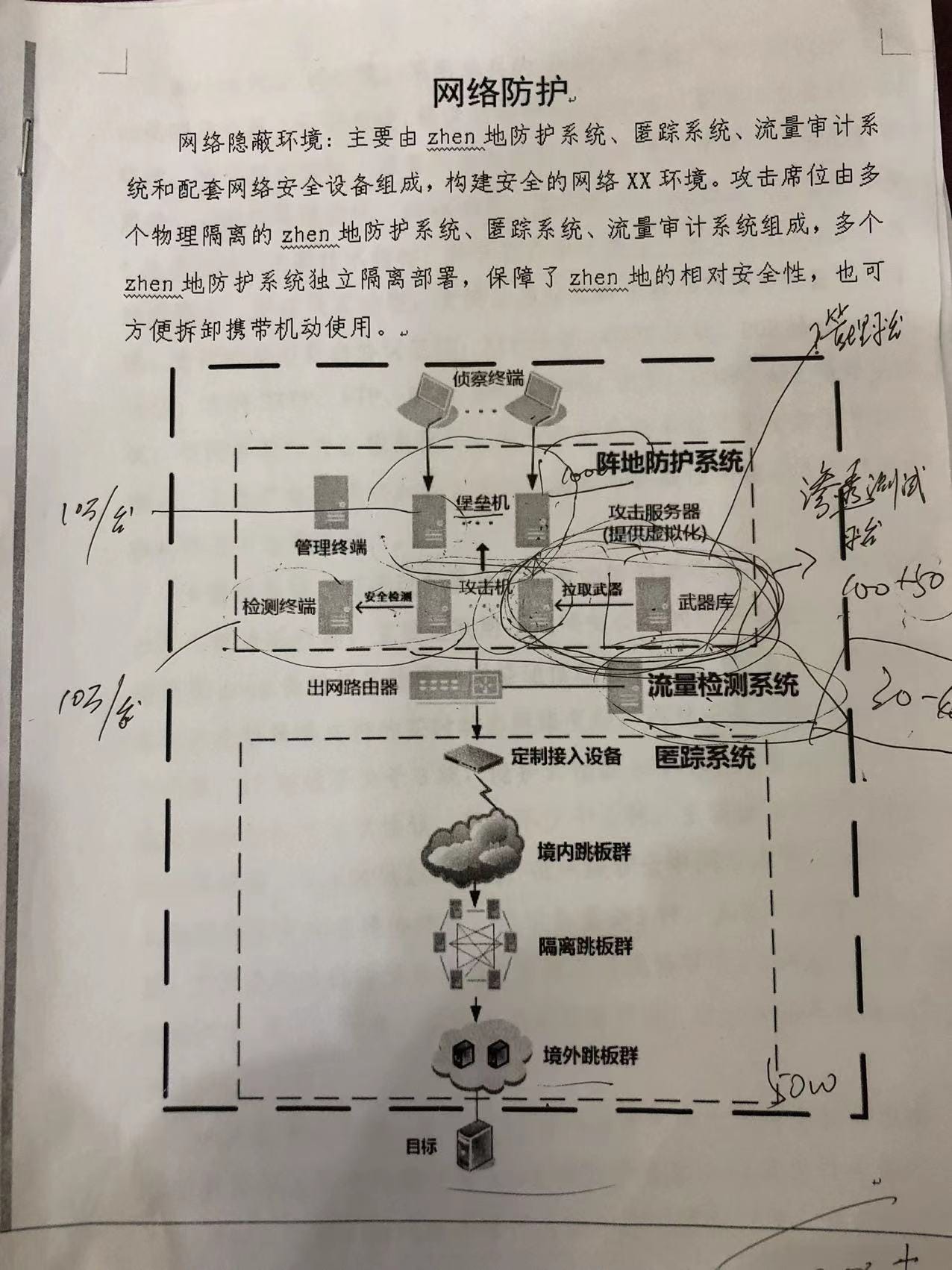
The introduction page already lays out a clear structure for the system’s technical design: a distributed network setup with a distinct separation between an “internal” system and several “external” components. We will break this down in detail later.
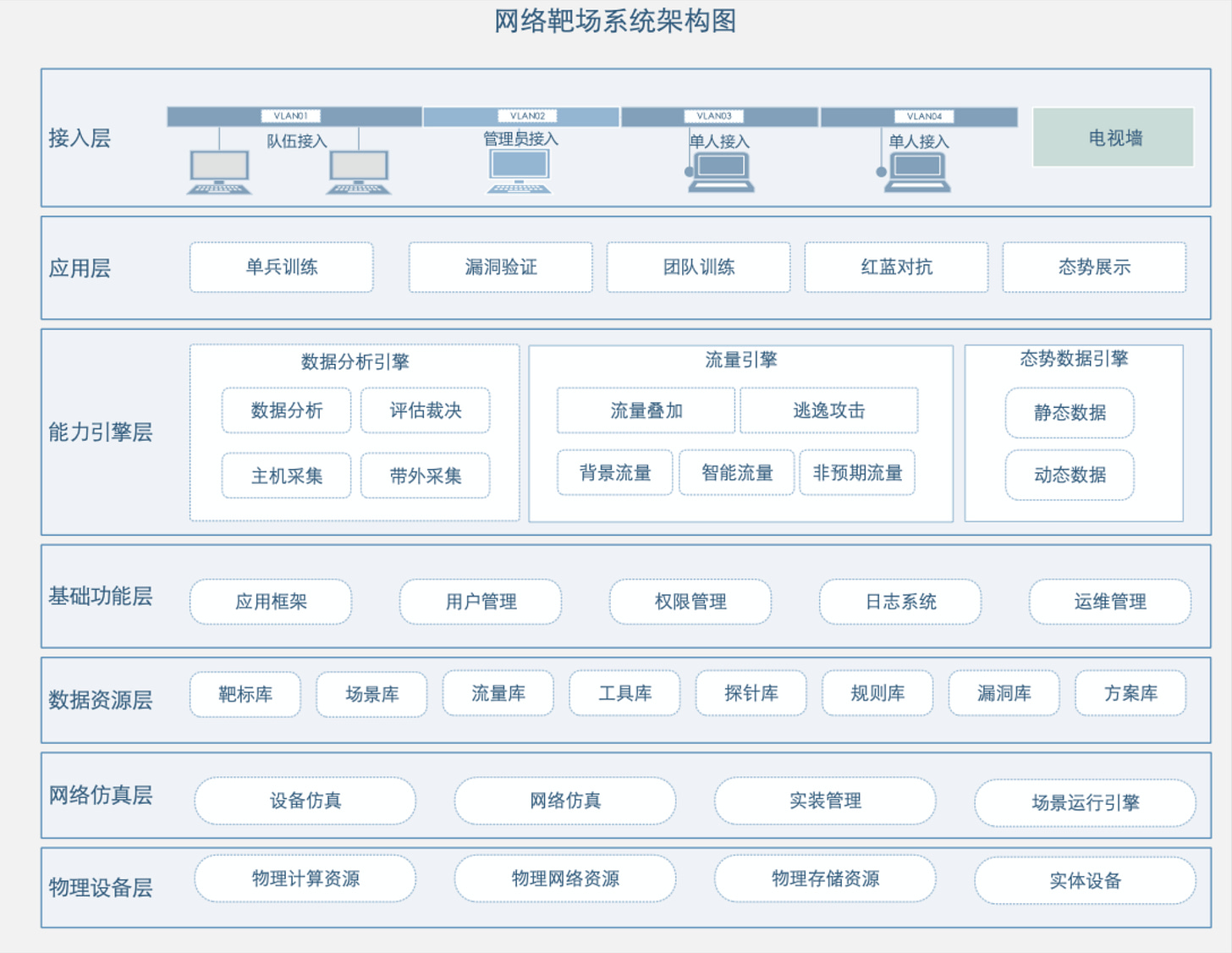
Page two outlines the system’s purpose: a network operations training environment capable of supporting 300 users and 10,000 concurrent connections. It includes DNS gateways, a URL classification database with 100 million entries, and support for 50,000 concurrent connections.
The system must record and monitor all traffic within its environment and between its components, and be able to identify network attacks and “malicious behavior.” It further states: “Based on operational applications, operational task requirements, and the technical methods of foreign cyberspace information action equipment, it is constructed according to the idea of realistic simulation and close to reality.”
This section introduces additional technical requirements. The system must provide both physical and logical isolation, support interconnection between fully virtualized routers and physical routers, and handle a selection of dynamic routing protocols.
The “client” appears particularly focused on the system’s stealth characteristics, emphasizing the need to shield its operations and infrastructure from outside detection:
“It can prevent network attacks from being tracked by deploying independent, private anti-piracy routes. Mainly utilizing the dense network systems of different network security companies to deploy hidden network communication lines for each network reconnaissance attack group.”
At the same time, the client demands an advanced anomaly-detection capability to uncover potential external intrusions in its own system.
This page contains something close to a smoking gun, offering crucial context for how this cyber range is meant to be used. A core component is an extensive library of templates that can be used to build target environments closely resembling the critical digital infrastructure of “major adversaries in the South China Sea and Indochina Peninsula.”
This phrasing makes it unmistakably clear: this is not a simple blue/red-team training platform for ordinary Chinese “cyber cops” chasing fraudsters or commercial hackers. It is a blueprint for an advanced training system designed to simulate attacks on a nation state's critical infrastructure.
The document also focuses on products from CISCO, Fortinet, WatchGuard, and Juniper as primary operational targets.
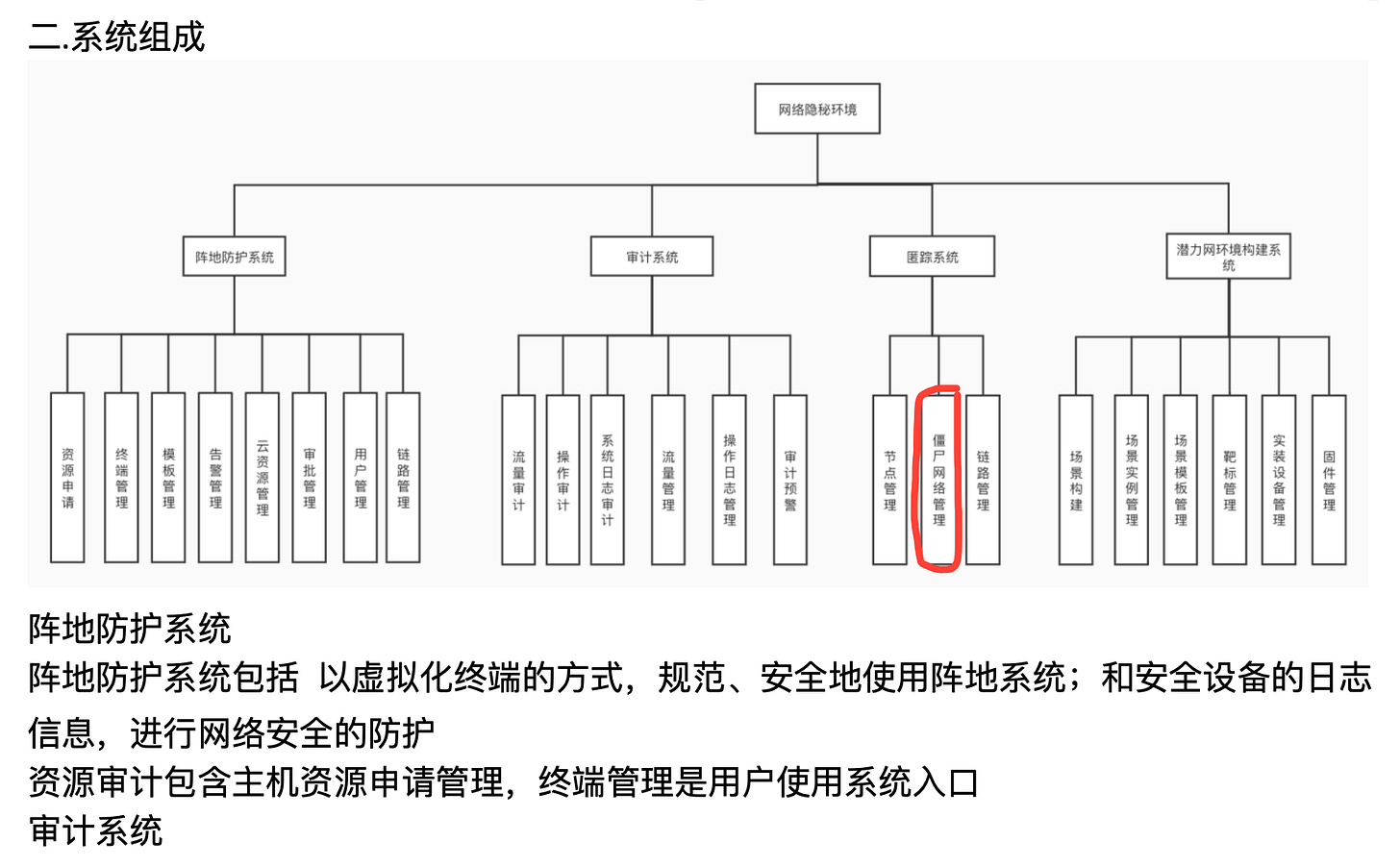
The file is stored in a folder named “九州需求,” which may indicate that the project was setup by Cyberpeace’s “Kyushu Attack and Defense Labs” (loosely translated). This appears to be an elite cybersecurity division within the company, also known for participating in CTF events as “mission adversaries”. As seen from above, a couple of phrases are in Latin letters instead of Chinese characters. Some are obviously company names, but others are “mix-words” like gong击机, APTgong击等 or 保障了zhen地的相对安全性. That could point towards intentional obfuscation to avoid keyword detection of sensitive terms.
The built
Next, we move into the technical details and design documents. The brief has already given us the framework and a long list of requirements. Now let’s look at how the system was actually designed around 2021.
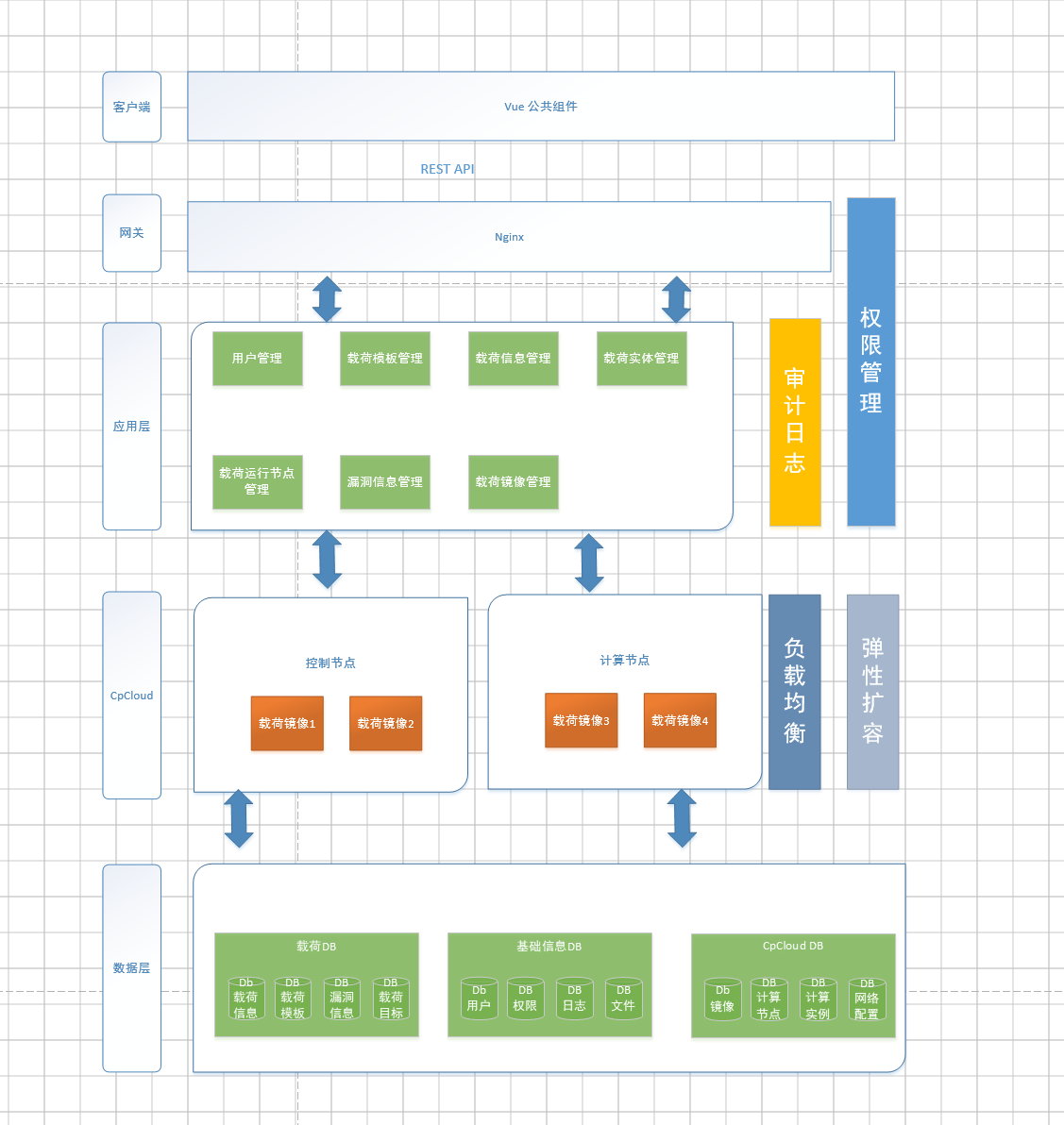
A general layout diagram outlining the system’s functionality and organizational structure reveals a fairly comprehensive cyber-range setup. Under “applications” (second box from the top), it lists: “individual training, team training, vulnerability research”, and “red/blue team confrontations”. It also incorporates extensive libraries for targets, tools, and known vulnerabilities.
The following screenshots are from one of Cyberpeace's own project assessment and summary documents:

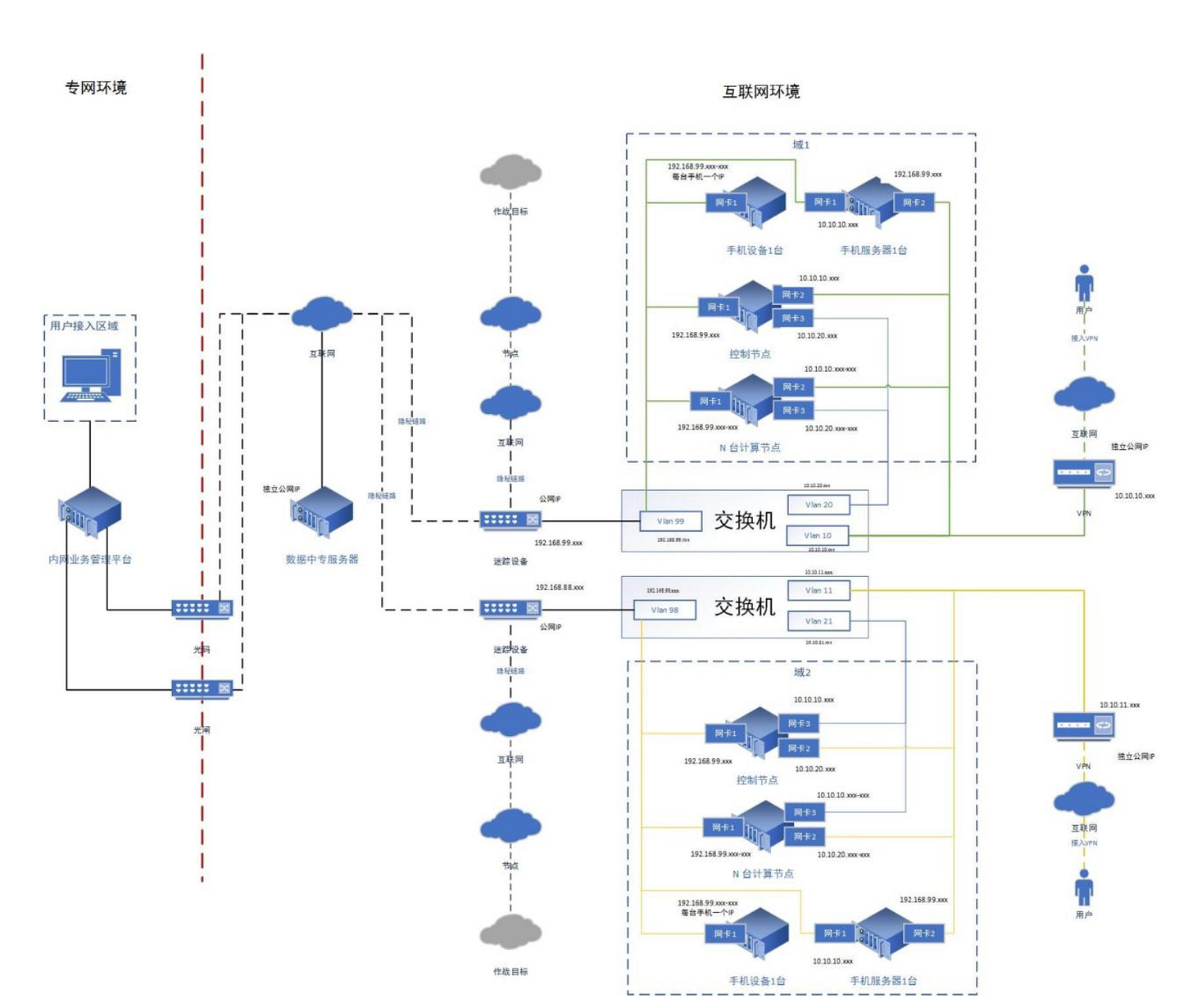
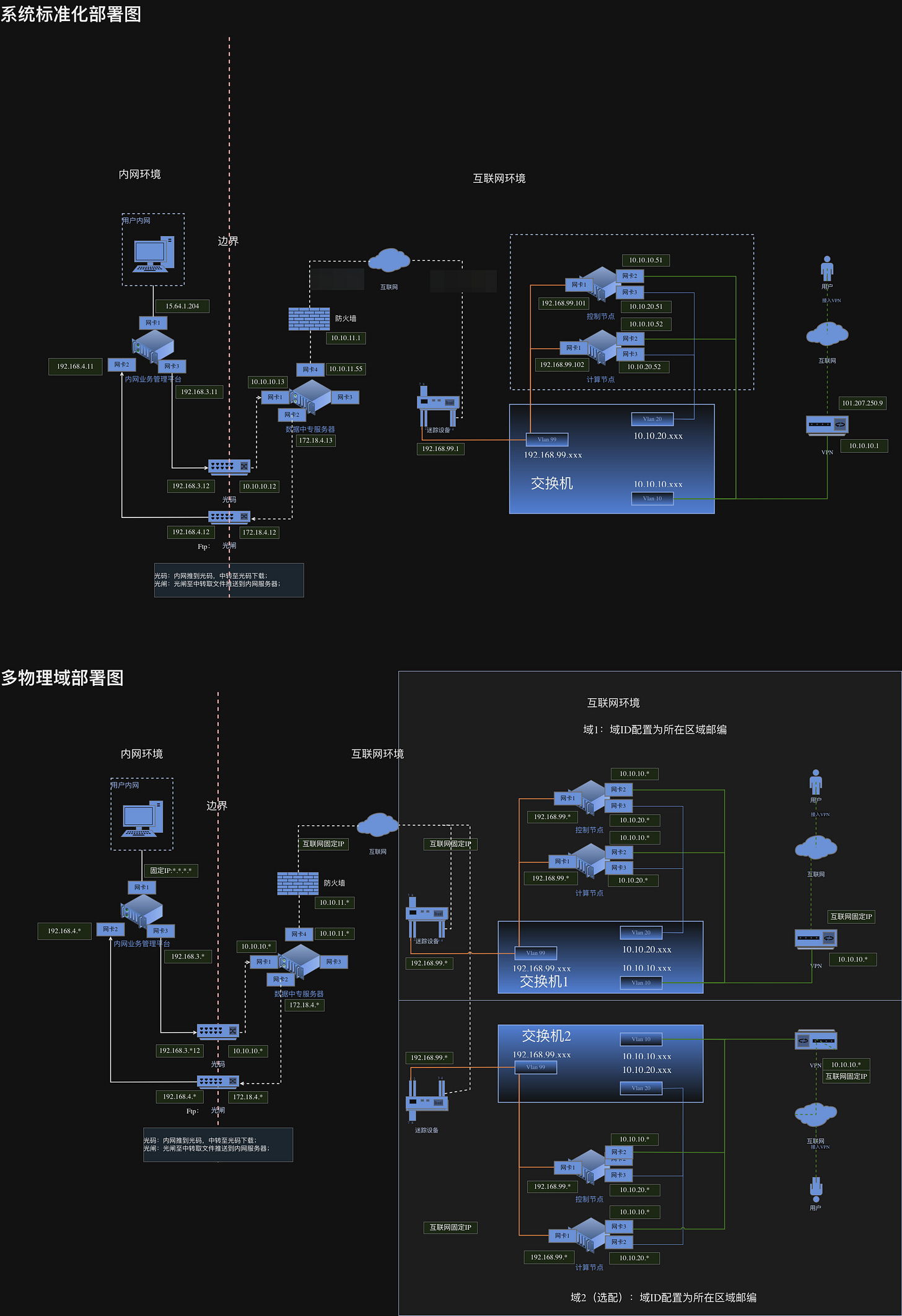
A detailed network layout shows clearly where this is all heading. We have two major sources that illustrate the overall network design: one from the “Installation Manual (安装部署手册)” and another from what appears to be an active UML diagram titled “Expedition Cloud Deployment Topology (远征云部署拓扑)”. Both describe the same system, but the latter provides a more granular view of a specific subsection within the larger architecture (see both below).
The system is divided into an “intranet” (I-N) and an “external network” (E-N). The intranet is where all data is ultimately assembled, stored and analyzed. Most active users also appear to connect from within the intranet. May it be the administrators, mission leaders or “operatives” (exception is the use of phones via an app for alternative admin control and user authentication).
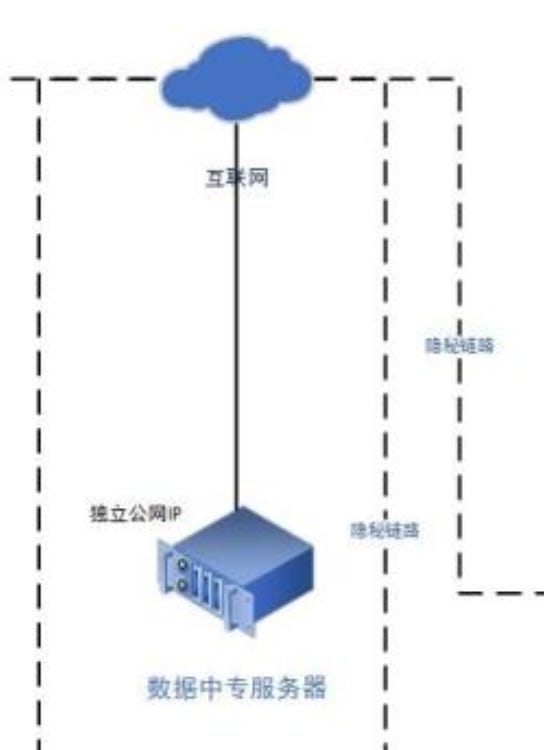
Data flowing from the I-N to the E-N is strictly controlled through “optical gates”, uni-directional data flow devices (an illustration of a possible device see below). This makes data extraction from the intranet significantly harder, even if the extra-net would be compromised.

The I-N’s role is data storage and heuristic analysis of logs and recordings. It also hosts the “weapons” library, user databases, scenario templates and other core assets. Architecturally, it seems to consist of a relatively straightforward collection of hosts and terminals.
The externals
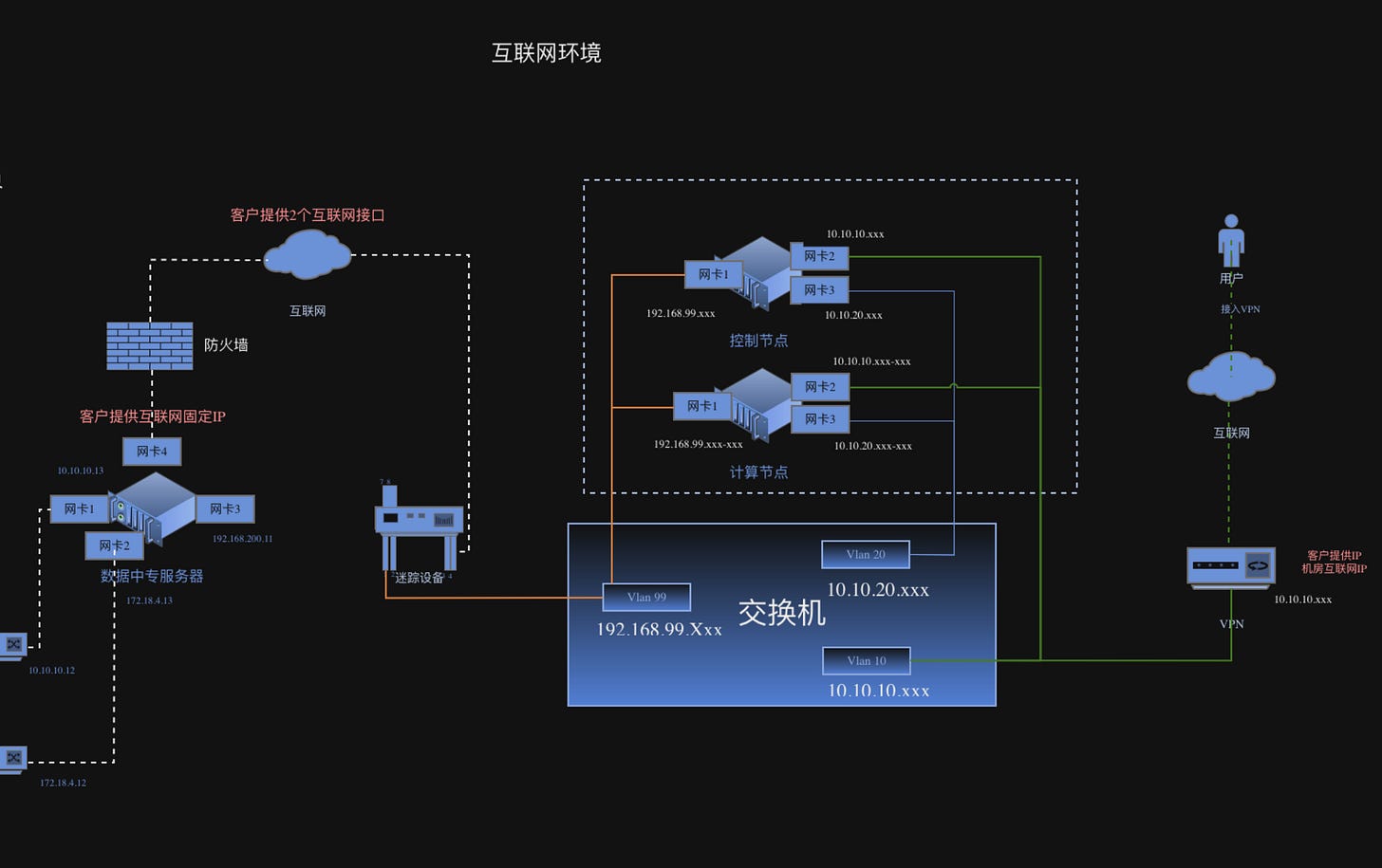
The E-N, by contrast, is more complex. Its first major component is the “relay” server; a sort of digital dead drop. It does not initiate data transfers on its own. Instead, it serves as a secure, anonymous temporary storage point. This way, the relay host itself has no direct access to other active components of the system.
The I-N interacts with this relay to upload and download operational data, as do other parts of the E-N. This gives the relay a deliberately passive nature. The idea appears to be that, if the relay were compromised, lateral movement would be extremely difficult, if not impossible.
It functions as the central pivot for the system’s heavier data communication elements (copying bigger files, logs, videos etc.). By design, it sits behind a firewall but remains reachable via the public internet via its own IP and domain.
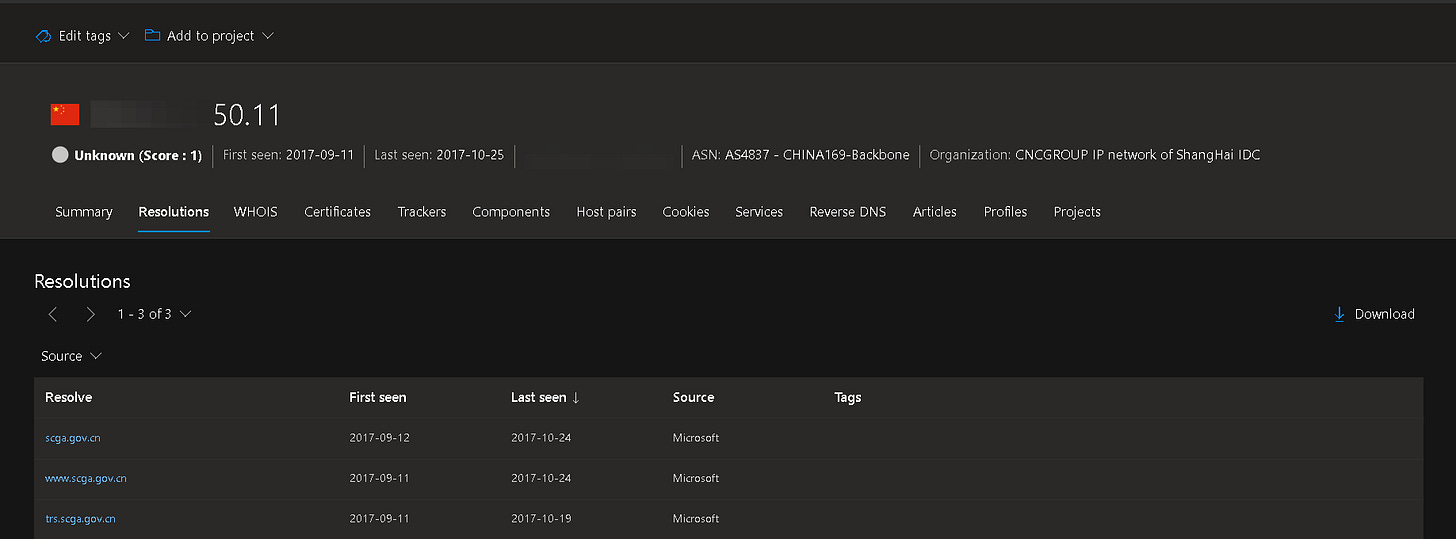
In fig. 2 above are a few public IP's mentioned (we have redacted for now). While testing, we found out that these hosts are still up-and-running in China. A historical IP/domain pairing traces one of the IPs back to a domain once operated by the Sichuan Public Security Bureau (“scga.gov.cn”).
It’s unclear whether that IPv4 address remains linked to the system as of today. The documents are already 3 to 4 years old, but Shodan records suggest the host is heavily firewalled.
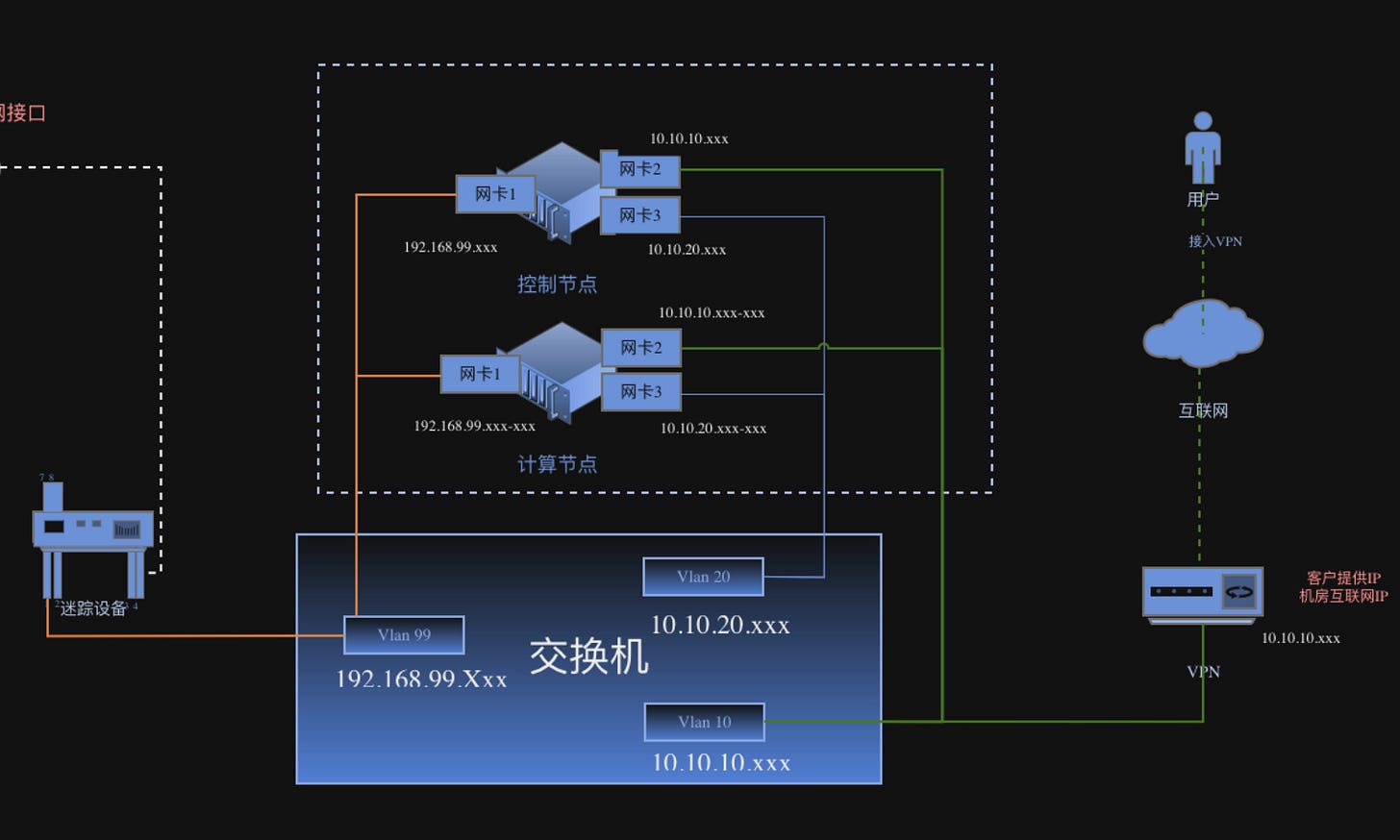
Next are the workhorses of the E-N: the worker nodes (W-N). Distributed globally, each consists of a “data node” and a “compute node.” The client brief mentions a requirement of 200 that use at least three encrypted protocols to establish a secure communication between other parts of the system. Each worker node is exposed to the public internet through a single IP address. Its data inflow and outflow are heavily segmented across three internal virtual network segments (VLAN).
A final component is a “phone” app, connected to each W-N via a VPN that provides access those internal VLANs. Each W-N appears capable of supporting only a single phone connection and is reachable through just one IP/domain, something that becomes clear later on in our upcoming follow up next week.
We also see several “operations” or “targets” in the installation manual diagram. These targets are systems running on Virtual Private Servers that simulate the potential target environment, defined via aforementioned templates (see above).
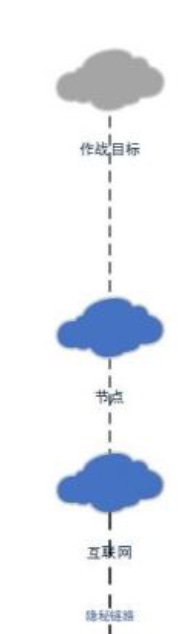
Last but not least are the “covert links” tying together the major E-N elements (the W-N, targets and the relay). This is a little bit of a “mysterious” component. While we have a reasonable idea of its purpose, detailed documentation is scarce, despite frequent references across all documents. Most likely it is just a conceptional term to describe that the W-N are not easily detectable on the public internet. But we will take about it some more later.
I hope this excursion has raised the appetite for more. In the next post we will do a deeper dive into each technical element, a little bit of source code and more documentation. Including some references to servers in the US and Israel. I promise, it will be worth it.
Teaser: A first glimpse of UML that is included in the documents we base our further technical analysis on in Part 2.
Read PART 2 here:
If you have more information on this story either write to us here or use our dead drop under deaddrop.netaskari.online








The detail is quite badass on this. Man… I do feel like we are behind the 8 ball. Or… I don’t know enough and it scares me.